Android Studio: Security
Sumber: https://source.android.com/devices/tech/security/
Android adalah platform mobile modern yang dirancang untuk menjadi benar-benar terbuka. Aplikasi android menggunakan hardware canggih dan software, serta data lokal dan disajikan, ter-expose melalui platform untuk membawa inovasi dan nilai kepada konsumen. Untuk melindungi nilai tersebut, platform harus menawarkan lingkungan aplikasi yang menjamin keamanan pengguna, data, aplikasi, perangkat, dan jaringan.
Mengamankan platform terbuka memerlukan arsitektur keamanan yang kuat dan program keamanan yang ketat. Android dirancang dengan keamanan berlapis-lapis yang menyediakan fleksibilitas yang diperlukan untuk platform terbuka, sambil memberikan perlindungan bagi semua pengguna platform. Untuk informasi tentang pelaporan masalah keamanan dan proses update, lihat Security Updates and Resources.
Android dirancang dengan developer dalam pikiran. Kontrol keamanan yang dirancang untuk mengurangi beban pengembang. Developer yang familiar dengan keamanan dapat dengan mudah bekerja dengan dan bergantung pada kontrol keamanan yang fleksibel. Pengembang kurang familiar dengan keamanan akan dilindungi oleh default yang aman.
Android dirancang dengan pengguna perangkat dalam pikiran. Pengguna disediakan visibilitas ke bagaimana aplikasi bekerja, dan kontrol atas aplikasi mereka. Desain ini meliputi perkiraan bahwa penyerang akan mencoba untuk melakukan serangan umum, seperti serangan rekayasa sosial untuk meyakinkan pengguna perangkat untuk menginstal malware, dan serangan terhadap aplikasi pihak ketiga di Android. Android dirancang untuk mengurangi kemungkinan serangan ini dan sangat membatasi dampak serangan jika hal itu terjadi.
Dokumentasi ini menguraikan tujuan dari program keamanan Android, menjelaskan dasar-dasar arsitektur keamanan Android, dan menjawab pertanyaan-pertanyaan yang paling relevan untuk arsitek sistem dan analis keamanan. Dokumen ini berfokus pada fitur keamanan platform inti Android dan tidak membahas masalah keamanan yang unik untuk aplikasi tertentu, seperti yang terkait dengan aplikasi browser atau SMS. Praktik terbaik yang direkomendasikan untuk membangun perangkat Android, penggelaran perangkat Android, atau mengembangkan aplikasi untuk Android tidak tujuan dokumen ini dan disediakan tempat lain.
Latar Belakang
Android provides an open source platform and application environment for mobile devices.
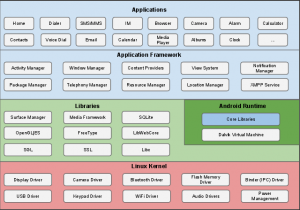
The sections and pages below describe the security features of the Android platform. Figure 1 summarizes the security components and considerations of the various levels of the Android software stack. Each component assumes that the components below are properly secured. With the exception of a small amount of Android OS code running as root, all code above the Linux Kernel is restricted by the Application Sandbox.
Building block utama dari Android Platform adalah:
- Device Hardware: Android runs on a wide range of hardware configurations including smart phones, tablets, and set-top-boxes. Android is processor-agnostic, but it does take advantage of some hardware-specific security capabilities such as ARM v6 eXecute-Never.
- Android Operating System: The core operating system is built on top of the Linux kernel. All device resources, like camera functions, GPS data, Bluetooth functions, telephony functions, network connections, etc. are accessed through the operating system.
- Android Application Runtime: Android applications are most often written in the Java programming language and run in the Dalvik virtual machine. However, many applications, including core Android services and applications are native applications or include native libraries. Both Dalvik and native applications run within the same security environment, contained within the Application Sandbox. Applications get a dedicated part of the filesystem in which they can write private data, including databases and raw files.
Android applications extend the core Android operating system. There are two primary sources for applications:
- Pre-Installed Applications: Android includes a set of pre-installed applications including phone, email, calendar, web browser, and contacts. These function both as user applications and to provide key device capabilities that can be accessed by other applications. Pre-installed applications may be part of the open source Android platform, or they may be developed by an OEM for a specific device.
- User-Installed Applications: Android provides an open development environment supporting any third-party application. Google Play offers users hundreds of thousands of applications.
Google provides a set of cloud-based services that are available to any compatible Android device. The primary services are:
- Google Play: Google Play is a collection of services that allow users to discover, install, and purchase applications from their Android device or the web. Google Play makes it easy for developers to reach Android users and potential customers. Google Play also provides community review, application license verification, application security scanning, and other security services.
- Android Updates: The Android update service delivers new capabilities and security updates to Android devices, including updates through the web or over the air (OTA).
- Application Services: Frameworks that allow Android applications to use cloud capabilities such as (backing up) application data and settings and cloud-to-device messaging (C2DM) for push messaging.
These services are not part of the Android Open Source Project and are out of scope for this document. But they are relevant to the security of most Android devices, so a related security document titled “Google Services for Android: Security Overview” is available.
Security updates and resources
Note: The preferred way to report security issues is sending an email detailing the issue to security@android.com.
Any developer, Android user, or security researcher can notify the Android security team of potential security issues. Your message can be encrypted using the Android security team PGP key here.
Sending an email to security@android.com is preferable to using the public Android bug tracker. Bugs marked as security issues are not externally visible, but they may eventually be made visible. If you plan to submit a patch to resolve a security issue, please contact security@android.com and wait for a response before submitting the patch to AOSP. Android Updates
Android provides system updates for both security and feature related purposes.
There are two ways to update the code on most Android devices: over-the-air (OTA updates) or side-loaded updates. OTA updates can be rolled out over a defined time period or be pushed to all devices at once, depending on how the OEM and/or carrier would like to push the updates. Side-loaded updates can be provided from a central location for users to download as a zip file to their local desktop machine or directly to their handset. Once the update is copied or downloaded to the SD card on the device, Android will recognize the update, verify its integrity and authenticity, and automatically update the device.
If a dangerous vulnerability is discovered internally or responsibly reported to Google or the Android Open Source Project, the Android security team will start the following process.
- The Android team will notify companies who have signed NDAs regarding the problem and begin discussing the solution.
- The owners of code will begin the fix.
- The Android team will fix Android-related security issues.
- When a patch is available, the fix is provided to the NDA companies.
- The Android team will publish the patch in the Android Open Source Project
- OEM/carrier will push an update to customers.
The NDA is required to ensure that the security issue does not become public prior to availabilty of a fix and put users at risk. Many OHA members run their own code on Android devices such as the bootloader, wifi drivers, and the radio. Once the Android Security team is notified of a security issue in this partner code, they will consult with OHA partners to quickly find a fix for the problem at hand and similar problems. However, the OHA member who wrote the faulty code is ultimately responsible for fixing the problem.
If a dangerous vulnerability is not responsibly disclosed (e.g., if it is posted to a public forum without warning), then Google and/or the Android Open Source Project will work as quickly as possible to create a patch. The patch will released to the public (and any partners) when the patch is tested and ready for use.
At Google I/O 2011, many of the largest OHA partners committed to providing updates to devices for 18 months after initial shipment. This will provide users with access to the most recent Android features, as well as security updates.
Any developer, Android user, or security researcher can notify the Android security team of potential security issues by sending email to security@android.com. If desired, communication can be encrypted using the Android security team PGP key available here: https://developer.android.com/security_at_android_dot_com.txt.
Other Resources
- Information for Android application developers is here: https://developer.android.com.
- The Android Security team can be reached at security@android.com.
- Security information exists throughout the Android Open Source and Developer Sites. A good place to start is here: https://developer.android.com/guide/topics/security/security.html.
- A Security FAQ for developers is located here: https://developer.android.com/resources/faq/security.html.
- Security Best Practices for developers is located here: https://developer.android.com/guide/practices/security.html.
- A community resource for discussion about Android security exists here: https://groups.google.com/forum/?fromgroups#!forum/android-security-discuss.