Difference between revisions of "WiFi: HotSpot - CoovaChilli Pendahuluan"
Onnowpurbo (talk | contribs) |
Onnowpurbo (talk | contribs) |
||
| Line 1: | Line 1: | ||
[[Image:Chilli 2.preview.jpg|right|200px|thumb]] | [[Image:Chilli 2.preview.jpg|right|200px|thumb]] | ||
| − | + | CoovaChilli adalah sebuah [[software]] access controller [[open source]], berbasis pada Chillispot project yang sekarang sudah tidak aktif. CoovaChilli aktif di kembangkan oleh kontributor Chillispot. | |
| − | CoovaChilli | + | CoovaChilli adalah sebuah [[software]] access control yang kaya akan fitur, yang dapat memberikan [[captive portal]] / walled-garden environment dan menggunakan RADIUS untuk mengontrol akses dan akunting. CoovaChilli adalah bagian integral dari [[firmware]] CoovaAP OpenWRT. |
| − | + | ==Kebutuhan== | |
| − | + | Tutorial ini akan memperlihatkan bagaimana menjalankan [[software]] ini di sebuah mesin. Pada dasarnya, anda dapat menginstalasi Apache, MySQL, dan FreeRADIUS di mesin yang berbeda. Anda hanya perlu mengkonfigursi masing-masing parameter dari [[software]] tersebut. Biasanya, CoovaChilli di jalankan di [[router]] - menggunakan [[firmware]] seperti OpenWrt (atau CoovaAP), SDK vendor (seperti Ubiquiti), atau pre-install [[hardware]] seperti FON atau open-mesh.com. | |
| − | + | CATATAN: baik coovachilli dan chillispot tidak dapat bekerja di [[OS]] 64 bit. Authentikasi RADIUS bermasalah di setup tersebut. | |
| − | + | HOWTO ini mengasumsikan bahwa kita mempunyai sebuah mesin x86 dengan dua [[network interface]]. Biasanya, satu menjadi interface [[WAN]], dan "subscriber" [[LAN]] [[interface]] yang akan di kontrol oleh CoovaChilli. [[Interface]] ini dapat berupa [[ethernet]] atau [[WiFi]]. Dalam contoh ini, kita akan mengasumsikan dua [[interface]] [[Ethernet]] untuk [[WAN]] (eth0) dan [[LAN]] (eth1). | |
| − | + | ==Proses== | |
| − | + | CoovaChilli akan mengambik alih control dari internal interface (eth1) menggunakan socket raw promiscuous. CoovaChilli kemudian akan menggunakan [[kernel]] modul vtun untuk membangun [[interface]] virtual (bisa tun au tap) untuk meneruskan packet yang di terima atau di kirim ke [[WAN]]. Pada dasarnya, kernel modul vtun digunakan untuk memindahkan paket [[IP]] dari kernel ke mode user, sedemikkan hingga CoovaChilli dapat berfungsi tanpa non-standard kernel module. CoovaChilli kemudian akan memberikan [[DHCP]], [[ARP]], and [[HTTP]] Hijacking pada interface "dhcpif", pada kasus kita adalah eth0. | |
| − | |||
| − | |||
| − | |||
| − | |||
A client connecting to this interface is limited to a "walled garden" until authorized. The client is only able to resolve DNS and web browser web sites specifically added to the walled garden. Authentication (and authorization) in CoovaChilli typically happens in one of two ways. Either it was a MAC based authentication (using the macauth option in chilli.conf) or it was the more typical "Universal Access Method" (UAM). This method uses a captive portal that initiates authentication. When a non-authenticated client tries to connect to a web-page (on port 80) the request is intercepted by CoovaChilli and redirected to the captive portal. In our case, we'll use a perl-script called hotspotlogin.cgi (served by apache over https). | A client connecting to this interface is limited to a "walled garden" until authorized. The client is only able to resolve DNS and web browser web sites specifically added to the walled garden. Authentication (and authorization) in CoovaChilli typically happens in one of two ways. Either it was a MAC based authentication (using the macauth option in chilli.conf) or it was the more typical "Universal Access Method" (UAM). This method uses a captive portal that initiates authentication. When a non-authenticated client tries to connect to a web-page (on port 80) the request is intercepted by CoovaChilli and redirected to the captive portal. In our case, we'll use a perl-script called hotspotlogin.cgi (served by apache over https). | ||
| Line 26: | Line 22: | ||
A user is then either rejected or authenticated by FreeRADIUS, prompting hotspotlogin.cgi to present either a rejection message or a page with a success message and a logout link to the user. | A user is then either rejected or authenticated by FreeRADIUS, prompting hotspotlogin.cgi to present either a rejection message or a page with a success message and a logout link to the user. | ||
| + | |||
| + | |||
| + | ==Pranala Menarik== | ||
| + | |||
| + | * [[WiFi: HotSpot]] | ||
Revision as of 05:25, 6 March 2010
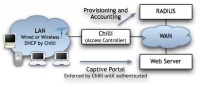
CoovaChilli adalah sebuah software access controller open source, berbasis pada Chillispot project yang sekarang sudah tidak aktif. CoovaChilli aktif di kembangkan oleh kontributor Chillispot.
CoovaChilli adalah sebuah software access control yang kaya akan fitur, yang dapat memberikan captive portal / walled-garden environment dan menggunakan RADIUS untuk mengontrol akses dan akunting. CoovaChilli adalah bagian integral dari firmware CoovaAP OpenWRT.
Kebutuhan
Tutorial ini akan memperlihatkan bagaimana menjalankan software ini di sebuah mesin. Pada dasarnya, anda dapat menginstalasi Apache, MySQL, dan FreeRADIUS di mesin yang berbeda. Anda hanya perlu mengkonfigursi masing-masing parameter dari software tersebut. Biasanya, CoovaChilli di jalankan di router - menggunakan firmware seperti OpenWrt (atau CoovaAP), SDK vendor (seperti Ubiquiti), atau pre-install hardware seperti FON atau open-mesh.com.
CATATAN: baik coovachilli dan chillispot tidak dapat bekerja di OS 64 bit. Authentikasi RADIUS bermasalah di setup tersebut.
HOWTO ini mengasumsikan bahwa kita mempunyai sebuah mesin x86 dengan dua network interface. Biasanya, satu menjadi interface WAN, dan "subscriber" LAN interface yang akan di kontrol oleh CoovaChilli. Interface ini dapat berupa ethernet atau WiFi. Dalam contoh ini, kita akan mengasumsikan dua interface Ethernet untuk WAN (eth0) dan LAN (eth1).
Proses
CoovaChilli akan mengambik alih control dari internal interface (eth1) menggunakan socket raw promiscuous. CoovaChilli kemudian akan menggunakan kernel modul vtun untuk membangun interface virtual (bisa tun au tap) untuk meneruskan packet yang di terima atau di kirim ke WAN. Pada dasarnya, kernel modul vtun digunakan untuk memindahkan paket IP dari kernel ke mode user, sedemikkan hingga CoovaChilli dapat berfungsi tanpa non-standard kernel module. CoovaChilli kemudian akan memberikan DHCP, ARP, and HTTP Hijacking pada interface "dhcpif", pada kasus kita adalah eth0.
A client connecting to this interface is limited to a "walled garden" until authorized. The client is only able to resolve DNS and web browser web sites specifically added to the walled garden. Authentication (and authorization) in CoovaChilli typically happens in one of two ways. Either it was a MAC based authentication (using the macauth option in chilli.conf) or it was the more typical "Universal Access Method" (UAM). This method uses a captive portal that initiates authentication. When a non-authenticated client tries to connect to a web-page (on port 80) the request is intercepted by CoovaChilli and redirected to the captive portal. In our case, we'll use a perl-script called hotspotlogin.cgi (served by apache over https).
hotspotlogin.cgi serves a page to the end-user with a username and password field. These authentication data are then forwarded to the FreeRADIUS server, which matches them with information in it’s back-end (using either PAP, CHAP, or MSCHAPv2). The FreeRADIUS back-end in this case is mysql, but could be any number of services such as LDAP, Kerberos, unix passwd files or even Active Directory (probably).
A user is then either rejected or authenticated by FreeRADIUS, prompting hotspotlogin.cgi to present either a rejection message or a page with a success message and a logout link to the user.