Difference between revisions of "WiFi: HotSpot - CoovaChilli Pendahuluan"
Onnowpurbo (talk | contribs) (New page: Introduction CoovaChilli is an open-source software access controller, based on the popular (but now defunct) ChilliSpot project, and is actively maintained by an original ChilliSpot cont...) |
Onnowpurbo (talk | contribs) |
||
| Line 1: | Line 1: | ||
| + | [[Image:Chilli 2.preview.jpg|right|200px|thumb]] | ||
| + | |||
Introduction | Introduction | ||
Revision as of 06:50, 2 March 2010
Introduction
CoovaChilli is an open-source software access controller, based on the popular (but now defunct) ChilliSpot project, and is actively maintained by an original ChilliSpot contributor.
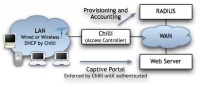
CoovaChilli is a feature rich software access controller that provides a captive portal / walled-garden environment and uses RADIUS for access provisioning and accounting. CoovaChilli is an integral part of the CoovaAP OpenWRT-based firmware which is specialized for hotspots. For more information on how Coova's Chilli differs from the standard ChilliSpot, see the ChangeLog.
Requirements
This tutorial will show how to run all this software on a single machine. However, you could install Apache, MySQL, and FreeRADIUS on a separate one, or even have 4 different machines: you'll just need to adjust the configuration parameters of each piece of software. Though, the more typical way to run CoovaChilli is on the router itself - using firmware such as OpenWrt (or CoovaAP), vendor SDKs (such as Ubiquiti), or pre-installed in hardware like that used by FON and open-mesh.com.
NOTE: both coovachilli and chillispot don't work with 64bit OS. RADIUS authentication is flawed in those setups.
Caveats
This HOWTO presumes you have an x86 machine with at least two physical network interfaces. Usually, this is an Ethernet WAN interface and "subscriber" LAN interface that CoovaChilli will control - it can be either a Ethernet or WiFi interface. In our case, we'll assume two Ethernet interfaces for the WAN (eth0) and LAN (eth1).
The proccess
CoovaChilli takes control of the internal interface (eth1) using a raw promiscuous socket. It then uses the vtun kernel module to bring up a virtual interface (either a tun or tap) to pass and receive packets to and from the WAN. In fact the vtun kernel module is used to move IP packets from the kernel to user mode, in such a way that CoovaChilli can function without any non-standard kernel modules. CoovaChilli then provides DHCP, ARP, and HTTP Hijacking on the "dhcpif" interface, in our case that's eth0.
A client connecting to this interface is limited to a "walled garden" until authorized. The client is only able to resolve DNS and web browser web sites specifically added to the walled garden. Authentication (and authorization) in CoovaChilli typically happens in one of two ways. Either it was a MAC based authentication (using the macauth option in chilli.conf) or it was the more typical "Universal Access Method" (UAM). This method uses a captive portal that initiates authentication. When a non-authenticated client tries to connect to a web-page (on port 80) the request is intercepted by CoovaChilli and redirected to the captive portal. In our case, we'll use a perl-script called hotspotlogin.cgi (served by apache over https).
hotspotlogin.cgi serves a page to the end-user with a username and password field. These authentication data are then forwarded to the FreeRADIUS server, which matches them with information in it’s back-end (using either PAP, CHAP, or MSCHAPv2). The FreeRADIUS back-end in this case is mysql, but could be any number of services such as LDAP, Kerberos, unix passwd files or even Active Directory (probably).
A user is then either rejected or authenticated by FreeRADIUS, prompting hotspotlogin.cgi to present either a rejection message or a page with a success message and a logout link to the user.