OpenWRT: VLAN
Sumber: https://www.lanis.nl/twiki/bin/view/Main/CreatingVLANsInOpenWRT
Creating and using VLANs in OpenWRT Backfire
Introduction
I have been struggling to create VLANs in OpenWRT Backfire (10.3) and couldn't really find the information I needed on the web. So I decided to write a brief summary of steps you need to take to set it up properly.
I personally own a Ubiquiti RouterStation Pro (I can recommend buying one, see http://www.ubnt.com/rspro), so this guide is written with a RouterStation Pro in mind. It might work on other hardware as well.
Configuration
The file you need to change to setup the VLANs for you is /etc/config/network. The default file looks something like this:
config interface loopback
option ifname lo
option proto static
option ipaddr 127.0.0.1
option netmask 255.0.0.0
config interface lan
option ifname eth1
option type bridge
option proto static
option ipaddr 192.168.1.1
option netmask 255.255.255.0
config interface wan
option ifname eth0
option proto dhcp
config switch
option name eth1
option reset 1
option enable_vlan 1
config switch_vlan
option device eth1
option vlan 1
option ports "0 1 2 3 4"
The internal switch is configured to use only 1 VLAN (vlan 1) on all ports (0 through 4). None of the ports on the switch is tagged, since there is no * or t after any of the ports in the switch_vlan configuration.
Tagging the internal interface
The first thing we need to do is activate tagging on the internal network port, connected to the CPU, port 0. Change the switch_vlan section to read:
config 'switch_vlan'
option 'device' 'eth1'
option 'vlan' '1'
option 'ports' '0* 1 2 3 4'
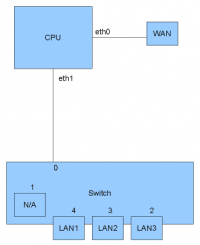
A picture will help explain this setup:
This is a simplified schematic of the inner workings of the RS Pro. As you can see eth0 connects to the internal switch. As far as I can tell the WAN port is not connected to the internal switch, but to a separate interface, eth1. Port 0 of the switch is connected to eth0. Port 1 of the switch is not connected and cannot be used. Ports 2 through 4 are connected to the LAN ports.
To be able to use separate VLANs, the switch needs to know which VLAN each port is on. This is accomplished by adding some extra information to each network packet leaving the CPU, the VLAN tag. The VLAN tag specifies which VLAN a packet belongs to (VLAN ID). Adding a VLAN tag to a network packets is called tagging. Adding a * after switchport 0 in the configuration file enables tagging and sets this port as the default VLAN (if no VLAN tag is present). The switch recognises the VLAN tag and uses the information in it to be able to send the packet to the right interface(s).
When booting with the above configuration, a new interface is created, named eth1.1, This is VLAN 1 on interface eth1. Use this interface in your network configuration:
config interface lan
option ifname eth1.1
option type bridge
option proto static
option ipaddr 192.168.1.1
option netmask 255.255.255.0
Creating a new VLAN
To create a new VLAN, we need to add a new section to the network configuration file, for example:
config 'switch_vlan'
option 'device' 'eth1'
option 'vlan' '2'
option 'ports' '0t'
This section adds a new interface to the router, named eth1.2, VLAN 2 on interface eth1. This VLAN is connected to port 0, the CPU, but not to any other ports. You will not be able to access this VLAN yet. You will also notice this VLAN is tagged, as specified by the t after port 0. Using a t instead of a *, enables tagging, but does not set the port to be the default VLAN (which is VLAN 1 in our configuration).
Assigning a VLAN to a port
To be able to access other VLANs we need to move ports from the default VLAN to another VLAN. For example:
config 'switch_vlan'
option 'device' 'eth1'
option 'vlan' '1'
option 'ports' '0* 1 3 4'
config 'switch_vlan'
option 'device' 'eth1'
option 'vlan' '2'
option 'ports' '0t 2'
Port 2 has been removed from the VLAN 1 configuration and added to the VLAN 2 configuration. Since port 2 is not tagged, the switch will remove any VLAN tags before sending out packets to port(s). Since no tagging is done on port 2, you can attach any computer to it and access the network like you normally would, without any regards for VLANs or VLAN tags.
Configuring the new VLAN interface
Having configured port 2 to connect to VLAN 2, we still need to configure an IP address on it. Add the following section to the network configuration file:
config 'interface' 'dmz'
option 'ifname' 'eth1.2'
option 'proto' 'static'
option 'netmask' '255.255.255.0'
option 'ipaddr' '192.168.2.1'
The interface name (dmz in this case) can be used with the config_get utility, to dynamically determine the interface, for example:
config_get DMZ dmz ifname
Adding this line to a script will set the variable $DMZ to the interfacename of the dmz interface, eth1.2 in our setup.
Configuring a port with multiple, tagged VLANs
I would recommend against using multiple VLANs on 1 machine, because it can become a routing nightmare.
It is also possible to assign more than 1 VLAN to a switch port. This port will need to be tagged and any computer connected to this port will need to be able to handle the VLAN tag. Lets change our setup, so port 2 is connected to VLAN 1 and VLAN 2:
config 'switch_vlan'
option 'device' 'eth1'
option 'vlan' '1'
option 'ports' '0* 1 2t 3 4'
config 'switch_vlan'
option 'device' 'eth1'
option 'vlan' '2'
option 'ports' '0t 2t'
As you can see port 2 is present in both VLAN configurations and is tagged in both places. To connect a Linux machine to this port and be able to access both VLANs, you need to install a packges called vconfig or vlan and set up multiple network configuration files, 1 for each VLAN you want to access. For example:
Gentoo (/etc/conf.d/net)
lans_eth0="1 2" config_eth0=( "null" ) vconfig_eth0=( "set_name_type VLAN_PLUS_VID_NO_PAD" ) config_vlan1=( "192.168.1.2/24" ) config_vlan2=( "192.168.2.2/24" )
Red Hat ES 5 / CentOS 5 (/etc/sysconfig/network-scripts/ifcfg-vlan2)
VLAN=yes VLAN_NAME_TYPE=VLAN_PLUS_VID_NO_PAD DEVICE=vlan2 PHYSDEV=eth0 BOOTPROTO=static ONBOOT=yes TYPE=Ethernet IPADDR=192.168.2.2 NETMASK=255.255.255.0
Debian / Ububtu (/etc/network/interfaces)
auto vlan2 iface vlan2 inet static address 192.168.2.2 netmask 255.255.255.0 network 192.168.2.0 broadcast 192.168.2.255 mtu 1500 vlan_raw_device eth0