Difference between revisions of "IPv6 Enkripsi: Mode untuk Enkripsi dan Authentikasi"
Onnowpurbo (talk | contribs) |
Onnowpurbo (talk | contribs) |
||
| (One intermediate revision by the same user not shown) | |||
| Line 13: | Line 13: | ||
Mode ini biasanya akan mengurangi MTU dengan 40 octet dari MTU mode transport. Jika menggunakan AES-128 untuk enkripsi dan SHA1 untuk authentikasi maka 82 octet akan di ambil dari MTU yang normal. | Mode ini biasanya akan mengurangi MTU dengan 40 octet dari MTU mode transport. Jika menggunakan AES-128 untuk enkripsi dan SHA1 untuk authentikasi maka 82 octet akan di ambil dari MTU yang normal. | ||
| + | |||
| + | ==IPv6 Packet Encryption== | ||
| + | |||
| + | IPsec defines cryptography-based security for both IPv4 and IPv6 in RFC 4301. IPsec support is an optional add-on in IPv4, but is a mandatory part of IPv6. It provides two security headers which can be used separately or together: Authentication Header (AH) and Encapsulating Security Payload (ESP), used in conjunction with security key exchange. | ||
| + | |||
| + | [[File:IPsecAHmodes.png|center|400px|thumb]] | ||
| + | |||
| + | ===Authentication Header=== | ||
| + | AH provides connectionless integrity, data-origin authentication and protection against replay attacks. It authenticates with an Integrity Check Value (ICV) calculated over the payload, the header, and unchanging fields of the IPv6 header and options. AH does not provide privacy and confidentiality of packet contents. See RFC 2402. | ||
| + | |||
| + | |||
| + | [[File:IPsecESPmodes.png|center|400px|thumb]] | ||
| + | |||
| + | ===Encapsulating Security Payload=== | ||
| + | ESP also provides connectionless integrity, data-origin authentication, protection against replay attacks, limited traffic flow confidentiality, but also provides privacy and confidentiality through encryption of the payload. See RFC 2406. | ||
| + | |||
| + | ===IPsec Modes=== | ||
| + | IPSec operates in two different modes: Transport mode (host-to-host) and Tunnel mode (gateway-to-gateway or gateway-to-host). | ||
| + | Transport mode: the IPv6 header of the original packet is used, followed by the AH or ESP header, then the payload. | ||
| + | Tunnel mode: a new IPv6 header encapsulates the AH or ESP header and the original IP header and payload. | ||
| + | Extension headers (Hop-by-Hop, Routing, Fragmentation) immediately follow their IP headers, except for Destination Options, which can appear before or after AH or ESP. ('TCP' below indicates any upper layer protocol.) | ||
| + | |||
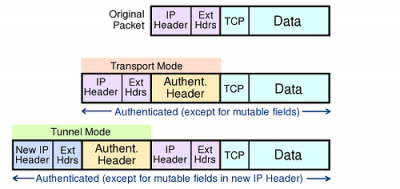
| + | ===Authentication Header Modes=== | ||
| + | ====AH in Transport & Tunnel Modes==== | ||
| + | AH authenticates the packet and the outermost IPv6 addresses (except for mutable fields), but does not encrypt payloads. AH cannot be used to traverse NATs, as it calculates the integrity check value (ICV) over source and destination addresses: NATs translate addresses, so would invalidate ICVs. | ||
| + | |||
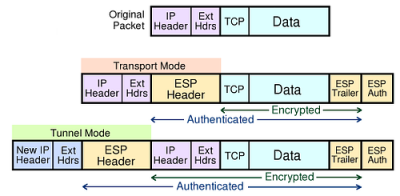
| + | ===Encapsulating Security Payload Modes=== | ||
| + | ====ESP in Transport & Tunnel Modes==== | ||
| + | ESP authentication does not include the outermost IPv6 headers, but in Tunnel mode it protects the original headers. ESP is used to build virtual private network tunnels between sites. It permits NAT traversal, as it does not use the outermost address values in the ICV calculation. If AH and ESP are used together, ESP is applied first, then AH authenticates the entire new packet. | ||
| + | |||
| + | ===The Security Association=== | ||
| + | Security Association is a record of the authentication algorithm, encryption algorithm, keys, mode (transport or tunnel), sequence number, overflow flag, expiry of the SA, and anti-replay window. The SA is held in a database at each endpoint, indexed by outer destination address, IPsec protocol (AH or ESP), and Security Parameter Index value. | ||
| + | |||
| + | Selection of SA can be manually (pre-shared keys) but preferably is automated with Internet Key Exchange (IKE, IKEv2). IKE uses Diffie-Hellman techniques to create a shared secret encryption key used to negotiate SA data. For key exchange, IKE depends on a Public Key Infrastructure (PKI), which is not yet widespread. The framework and syntax for key exchange is ISAKMP (Internet Security Association and Key Management Protocol). See RFC 2408. | ||
==Referensi== | ==Referensi== | ||
Latest revision as of 09:18, 13 December 2022
Dua mode yang mungkin digunakan untuk enkripsi dan authentikasi pada sebuah sambungan:
Mode Transport
Mode Transport adalah real end-to-end connection mode. Disini, hanya payload (biasanya ICMP, TCP atau UDP) yang di enkripsi dengan header mereka, sedang IP header tidak di enkrip (biasanya termasuk di authentikasi).
Menggunakan AES-128 untuk enkripsi dan SHA1 untuk authentikasi, mode ini akan mengurangi MTU sebanyak 42 octet.
Mode Tunnel
Mode Tunnel dapat digunakan baik untuk mode sambungan end-to-end atau untuk gateway-to-gateway. Di sini, paket IP secara lengkap akan di enkrip dan memperoleh tambahan header IP yang baru, sehingga menjadi paket IP yang baru. Mekanisme ini biasanya di kenal sebagai "enkapsulasi".
Mode ini biasanya akan mengurangi MTU dengan 40 octet dari MTU mode transport. Jika menggunakan AES-128 untuk enkripsi dan SHA1 untuk authentikasi maka 82 octet akan di ambil dari MTU yang normal.
IPv6 Packet Encryption
IPsec defines cryptography-based security for both IPv4 and IPv6 in RFC 4301. IPsec support is an optional add-on in IPv4, but is a mandatory part of IPv6. It provides two security headers which can be used separately or together: Authentication Header (AH) and Encapsulating Security Payload (ESP), used in conjunction with security key exchange.
Authentication Header
AH provides connectionless integrity, data-origin authentication and protection against replay attacks. It authenticates with an Integrity Check Value (ICV) calculated over the payload, the header, and unchanging fields of the IPv6 header and options. AH does not provide privacy and confidentiality of packet contents. See RFC 2402.
Encapsulating Security Payload
ESP also provides connectionless integrity, data-origin authentication, protection against replay attacks, limited traffic flow confidentiality, but also provides privacy and confidentiality through encryption of the payload. See RFC 2406.
IPsec Modes
IPSec operates in two different modes: Transport mode (host-to-host) and Tunnel mode (gateway-to-gateway or gateway-to-host). Transport mode: the IPv6 header of the original packet is used, followed by the AH or ESP header, then the payload. Tunnel mode: a new IPv6 header encapsulates the AH or ESP header and the original IP header and payload. Extension headers (Hop-by-Hop, Routing, Fragmentation) immediately follow their IP headers, except for Destination Options, which can appear before or after AH or ESP. ('TCP' below indicates any upper layer protocol.)
Authentication Header Modes
AH in Transport & Tunnel Modes
AH authenticates the packet and the outermost IPv6 addresses (except for mutable fields), but does not encrypt payloads. AH cannot be used to traverse NATs, as it calculates the integrity check value (ICV) over source and destination addresses: NATs translate addresses, so would invalidate ICVs.
Encapsulating Security Payload Modes
ESP in Transport & Tunnel Modes
ESP authentication does not include the outermost IPv6 headers, but in Tunnel mode it protects the original headers. ESP is used to build virtual private network tunnels between sites. It permits NAT traversal, as it does not use the outermost address values in the ICV calculation. If AH and ESP are used together, ESP is applied first, then AH authenticates the entire new packet.
The Security Association
Security Association is a record of the authentication algorithm, encryption algorithm, keys, mode (transport or tunnel), sequence number, overflow flag, expiry of the SA, and anti-replay window. The SA is held in a database at each endpoint, indexed by outer destination address, IPsec protocol (AH or ESP), and Security Parameter Index value.
Selection of SA can be manually (pre-shared keys) but preferably is automated with Internet Key Exchange (IKE, IKEv2). IKE uses Diffie-Hellman techniques to create a shared secret encryption key used to negotiate SA data. For key exchange, IKE depends on a Public Key Infrastructure (PKI), which is not yet widespread. The framework and syntax for key exchange is ISAKMP (Internet Security Association and Key Management Protocol). See RFC 2408.
Referensi