Difference between revisions of "Burp Suite: Burpsuite beginners tutorial"
Onnowpurbo (talk | contribs) |
Onnowpurbo (talk | contribs) |
||
| (15 intermediate revisions by the same user not shown) | |||
| Line 2: | Line 2: | ||
| − | + | Ini adalah tutorial pemula burpsuite. Burpsuite adalah kumpulan tool, ditulis dalam Java yang digunakan untuk melakukan berbagai tugas terkait keamanan jaringan. | |
| − | Burpsuite | + | Burpsuite dapat digunakan sebagai basic http proxy untuk intercept traffic untuk analysis dan playback, web application security scanner, tool untuk melakukan serangan otomatis terhadap aplikasi web, tool untuk menjaring seluruh situs web untuk mengidentifikasi permukaan serangan dan memiliki plugin API dengan banyak addons pihak ketiga tersedia! |
| − | + | Dalam tutorial dasar ini, akan dijelaskan cara menggunakan fitur dasar yang tersedia di edisi komunitas (versi gratis). Jika anda belum melakukannya, unduh burpsuite dari situs portswigger: https://portswigger.net/ atau gunakan Kali Linux yang sudah menyediakan burpsuite di dalam-nya. | |
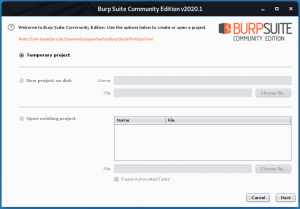
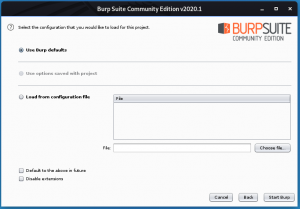
| − | + | Setelah menjalankan installer, pilih “new temporary project”, di ikuti dengan “use burp defaults”. | |
| − | [[File: | + | [[File:Screenshot from 2020-02-10 09-09-44.png|center|300px|thumb]] |
| − | [[File:Screenshot | + | [[File:Screenshot from 2020-02-10 09-11-05.png|center|300px|thumb]] |
| − | [[File:Screenshot 2018-04-07 18-58-49.png|center| | + | [[File:Screenshot 2018-04-07 18-58-49.png|center|300px|thumb]] |
| − | + | Click “Start Burp” | |
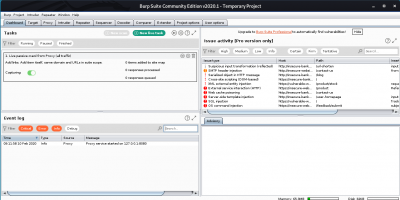
| − | + | Anda sekarang disajikan dengan interface utama dari burpsuite. | |
| − | [[File:Screenshot | + | [[File:Screenshot from 2020-02-10 09-13-00.png|center|400px|thumb]] |
| − | ==Burp | + | ==Burp sebagai HTTP Proxy== |
| − | + | Salah satu fitur yang paling banyak digunakan dalam burpsuite adalah http proxy. Ini memungkinkan anda untuk record, modify, playback dan explore permintaan http individual. Sebagai titik awal dalam tutorial ini kita akan menggunakan firefox dan secara manual memasukkan beberapa url untuk dijelajahi. | |
| − | + | Anda harus mengatur firefox (FF) untuk menggunakan proxy. Langkah melakukan ini: | |
| − | + | * Buka FF klik preferences > advanced > networking > connection [settings] > proxy | |
| − | + | * Di “httpp proxy” input box, masukan 127.0.0.1 sebagai IP address dan “8080” sebagai “port”. | |
| − | + | * tick checkbox untuk “use for all protocols” (untuk keperluan tutorial ini kita akan mengirimkan semua paket ke burpsuite) | |
| − | SSL | + | ==SSL certificate== |
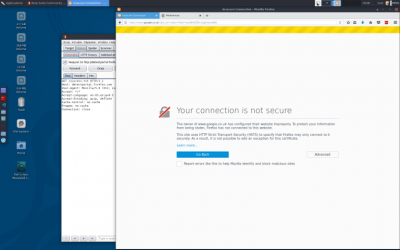
| − | + | Jika kita sekarang akses atau mencoba untuk akses situs yang dikonfigurasi dengan SSL (misalnya google.com), kita akan mendapatkan kesalahan ssl cert yang tidak valid, | |
[[File:Screenshot 2018-04-07 19-08-05.png|center|400px|thumb]] | [[File:Screenshot 2018-04-07 19-08-05.png|center|400px|thumb]] | ||
| − | + | Oleh karenanya, mengikuti langkah https://support.portswigger.net/customer/portal/articles/1783075-installing-burp-s-ca-certificate-in-your-browser kita akan install burp CA di browser kita. | |
| − | + | * akses http://burp di firefox | |
| − | + | * klik ‘CA Certificate’ di top menu bar | |
| − | + | * klik ‘save’ | |
| − | + | * klik Firefox > preferences > Advanced > certificates > view certificates > authorities > import | |
| − | + | * browse ke tempat anda download CA bundle. | |
| − | + | * Tick all the options. | |
| − | + | * klik OK | |
| − | + | * Di firefox addressbar, ketik “google.com” dan switch ke burpsuite. | |
[[File:Screenshot 2018-04-07 19-22-03.png|center|400px|thumb]] | [[File:Screenshot 2018-04-07 19-22-03.png|center|400px|thumb]] | ||
| Line 53: | Line 53: | ||
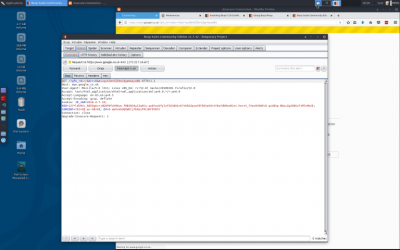
In the burpsuite tabs you can see the http headers, http parameters and the hex vaues if you need to (similar to the firefox inspector, but prior to the request being filled by the server) | In the burpsuite tabs you can see the http headers, http parameters and the hex vaues if you need to (similar to the firefox inspector, but prior to the request being filled by the server) | ||
| − | + | * at this point, nothing has been sent to the remote server! | |
| − | + | * click ‘forward’ | |
| − | + | * the request is sent to the server | |
| − | + | * You now have to switch to the ‘http history tab’ | |
[[File:Screenshot 2018-04-07 19-27-25.png|center|400px|thumb}} | [[File:Screenshot 2018-04-07 19-27-25.png|center|400px|thumb}} | ||
You can see the request that was sent, and also a tab with ‘response’ (there is a ‘raw’ output, and also a ‘render’ output – the render is very useful when looking for blindSQL) | You can see the request that was sent, and also a tab with ‘response’ (there is a ‘raw’ output, and also a ‘render’ output – the render is very useful when looking for blindSQL) | ||
| − | + | ||
| + | ==Melakukan attack== | ||
At this point you have the basics of burp. From here you can start on the advanced techniques (tbh upto this point we havent actually done anything yet, we just intercepted a request and forwarded it to the server) so, I’ll quickly show you how to intercept a request and modify it: | At this point you have the basics of burp. From here you can start on the advanced techniques (tbh upto this point we havent actually done anything yet, we just intercepted a request and forwarded it to the server) so, I’ll quickly show you how to intercept a request and modify it: | ||
| Line 73: | Line 74: | ||
Follow my instructions for setting up a local dvwa vagrant installation to safely perform all the following actions (if you set dvwa security to ‘impossible’ mode the attack here will fail, if its set to ‘low’) | Follow my instructions for setting up a local dvwa vagrant installation to safely perform all the following actions (if you set dvwa security to ‘impossible’ mode the attack here will fail, if its set to ‘low’) | ||
| − | + | * clear your current session in burp (quit burp and re-open) | |
| − | + | * set your firefox proxy to none, navigate to http://ip.address.of.dvwa.install/dvwa -verify its working | |
| − | + | * set your firefox to use burp as a proxy again | |
| − | Scope | + | ==Scope== |
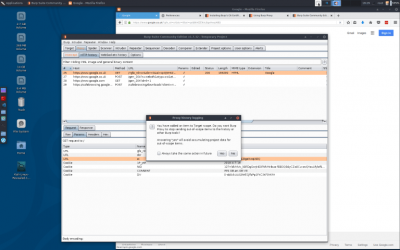
At this stage it is worth setting a ‘scope’ – currently we are logging everything from firefox into burp. This can become overwhelming fast! | At this stage it is worth setting a ‘scope’ – currently we are logging everything from firefox into burp. This can become overwhelming fast! | ||
| − | + | * navigate to http://ip.address.of.dvwa.install/dvwa | |
| − | + | * click ‘forward’ in the proxy tab of burpsuite | |
| − | + | * to set a scope, right click on the line in the history section for the dvwa request and select ‘add to scope’ | |
| − | + | * click yes when burp asks if you want to ignore requests out-of-scope | |
| − | + | [[File:Screenshot 2018-04-07 19-29-18.png|center|400px|thumb]] | |
This now means that we are only collecting urls for our dvwa install. | This now means that we are only collecting urls for our dvwa install. | ||
| − | Going further | + | |
| − | + | ==Going further== | |
| + | |||
| + | [[File:Dvwa-intercept-csrf.png|center|400px|thumb]] | ||
go back to the dvwa page in firefox (the login page should have loaded) | go back to the dvwa page in firefox (the login page should have loaded) | ||
| Line 98: | Line 101: | ||
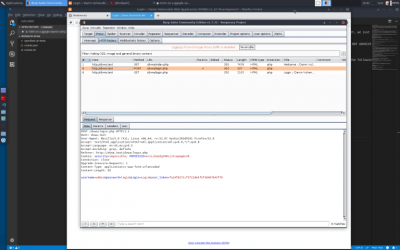
you’ll notice a request for dvwa with the parameter ‘username’ having a value of ‘admin | you’ll notice a request for dvwa with the parameter ‘username’ having a value of ‘admin | ||
| − | + | [[File:Dvwa-login-page-parameter-intercept.png|center|400px|thumb]] | |
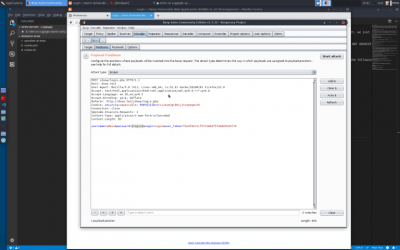
right-click in the area with the parameters and their values, and select “send to intruder” | right-click in the area with the parameters and their values, and select “send to intruder” | ||
| Line 104: | Line 107: | ||
in the ‘positions’ tab, click ‘clear’ | in the ‘positions’ tab, click ‘clear’ | ||
| − | + | [[File:Dvwa-intercept-positions.png|center|400px|thumb]] | |
highlight the value ‘login’ for the ‘password’ parameter and click ‘add’ on the right. | highlight the value ‘login’ for the ‘password’ parameter and click ‘add’ on the right. | ||
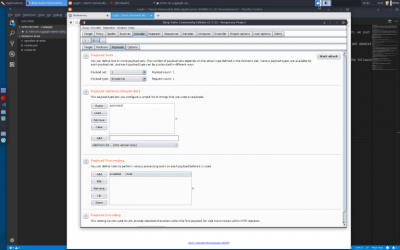
goto payloads | goto payloads | ||
| − | + | [[File:Dvwa-intercept-wordlist.png|center|400px|thumb]] | |
payload type: simple-list | payload type: simple-list | ||
payload options > add > type ‘password’ > click add | payload options > add > type ‘password’ > click add | ||
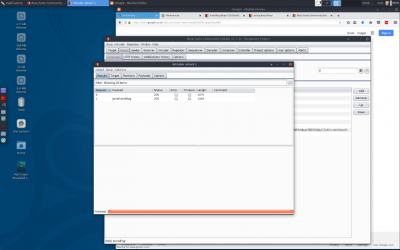
click ‘start attack’ | click ‘start attack’ | ||
| + | |||
| + | [[File:Screenshot 2018-04-07 20-06-01.png|center|400px|thumb]] | ||
click on request 1 | click on request 1 | ||
Latest revision as of 10:11, 10 February 2020
Sumber: https://jonathansblog.co.uk/burpsuite-beginners-tutorial
Ini adalah tutorial pemula burpsuite. Burpsuite adalah kumpulan tool, ditulis dalam Java yang digunakan untuk melakukan berbagai tugas terkait keamanan jaringan.
Burpsuite dapat digunakan sebagai basic http proxy untuk intercept traffic untuk analysis dan playback, web application security scanner, tool untuk melakukan serangan otomatis terhadap aplikasi web, tool untuk menjaring seluruh situs web untuk mengidentifikasi permukaan serangan dan memiliki plugin API dengan banyak addons pihak ketiga tersedia!
Dalam tutorial dasar ini, akan dijelaskan cara menggunakan fitur dasar yang tersedia di edisi komunitas (versi gratis). Jika anda belum melakukannya, unduh burpsuite dari situs portswigger: https://portswigger.net/ atau gunakan Kali Linux yang sudah menyediakan burpsuite di dalam-nya.
Setelah menjalankan installer, pilih “new temporary project”, di ikuti dengan “use burp defaults”.
Click “Start Burp”
Anda sekarang disajikan dengan interface utama dari burpsuite.
Burp sebagai HTTP Proxy
Salah satu fitur yang paling banyak digunakan dalam burpsuite adalah http proxy. Ini memungkinkan anda untuk record, modify, playback dan explore permintaan http individual. Sebagai titik awal dalam tutorial ini kita akan menggunakan firefox dan secara manual memasukkan beberapa url untuk dijelajahi.
Anda harus mengatur firefox (FF) untuk menggunakan proxy. Langkah melakukan ini:
- Buka FF klik preferences > advanced > networking > connection [settings] > proxy
- Di “httpp proxy” input box, masukan 127.0.0.1 sebagai IP address dan “8080” sebagai “port”.
- tick checkbox untuk “use for all protocols” (untuk keperluan tutorial ini kita akan mengirimkan semua paket ke burpsuite)
SSL certificate
Jika kita sekarang akses atau mencoba untuk akses situs yang dikonfigurasi dengan SSL (misalnya google.com), kita akan mendapatkan kesalahan ssl cert yang tidak valid,
Oleh karenanya, mengikuti langkah https://support.portswigger.net/customer/portal/articles/1783075-installing-burp-s-ca-certificate-in-your-browser kita akan install burp CA di browser kita.
- akses http://burp di firefox
- klik ‘CA Certificate’ di top menu bar
- klik ‘save’
- klik Firefox > preferences > Advanced > certificates > view certificates > authorities > import
- browse ke tempat anda download CA bundle.
- Tick all the options.
- klik OK
- Di firefox addressbar, ketik “google.com” dan switch ke burpsuite.
You may have a few captures for ‘firefox profile tracing’ – you can drop those by clicking the ‘drop’ button
In the burpsuite tabs you can see the http headers, http parameters and the hex vaues if you need to (similar to the firefox inspector, but prior to the request being filled by the server)
- at this point, nothing has been sent to the remote server!
- click ‘forward’
- the request is sent to the server
- You now have to switch to the ‘http history tab’
[[File:Screenshot 2018-04-07 19-27-25.png|center|400px|thumb}}
You can see the request that was sent, and also a tab with ‘response’ (there is a ‘raw’ output, and also a ‘render’ output – the render is very useful when looking for blindSQL)
Melakukan attack
At this point you have the basics of burp. From here you can start on the advanced techniques (tbh upto this point we havent actually done anything yet, we just intercepted a request and forwarded it to the server) so, I’ll quickly show you how to intercept a request and modify it:
“***** WARNING – IF YOU DO ANYTHING OTHER THAN TEST AGAINST YOUR LOCAL VAGRANT INSTALL OF DVWA THEN I AM NOT RESPONSIBLE AND YOU WILL GET CAUGHT, I AM NOT ADVOCATING ATTACKING ANYONE, I AM DEMONSTRATING MODIFYIG A REQUEST PARAMETER AGAINST A LOCAL DVWA INSTALL FOR A BASIC QUERY FOR THE PURPOSES OF EDUCATING THE READER TO ENABLE HIM/HER/THEY TO TEST AND SECURE THEIR OWN SYSTEMS*********
- if its your own service, or a vagrant box running in localhost, go ahead and try to break it *******
At this stage burpsuite is ready to go, but we have nothing to safely test against.
Follow my instructions for setting up a local dvwa vagrant installation to safely perform all the following actions (if you set dvwa security to ‘impossible’ mode the attack here will fail, if its set to ‘low’)
- clear your current session in burp (quit burp and re-open)
- set your firefox proxy to none, navigate to http://ip.address.of.dvwa.install/dvwa -verify its working
- set your firefox to use burp as a proxy again
Scope
At this stage it is worth setting a ‘scope’ – currently we are logging everything from firefox into burp. This can become overwhelming fast!
- navigate to http://ip.address.of.dvwa.install/dvwa
- click ‘forward’ in the proxy tab of burpsuite
- to set a scope, right click on the line in the history section for the dvwa request and select ‘add to scope’
- click yes when burp asks if you want to ignore requests out-of-scope
This now means that we are only collecting urls for our dvwa install.
Going further
go back to the dvwa page in firefox (the login page should have loaded) type ‘admin’ into the username box and ‘login’ in the password box. press enter; switch to burpsuite open the proxy > intercept tab you’ll notice a request for dvwa with the parameter ‘username’ having a value of ‘admin
right-click in the area with the parameters and their values, and select “send to intruder” goto the intruder tab in the ‘positions’ tab, click ‘clear’
highlight the value ‘login’ for the ‘password’ parameter and click ‘add’ on the right. goto payloads
payload type: simple-list payload options > add > type ‘password’ > click add click ‘start attack’
click on request 1 click on result you can see the results now if it shows a 302 redirect to the login page, our attack was unsuccessful if it shows a 302 redirect to the index page, our attack was successful go back to the firefox tab you initiated the query from
if you set dvwa in imposible security mode you should now see that the request failed because the csrf token did not match! if you set dvwa in low security mode you should see the control panel
I hope you enjoyed this burpsuite beginners tutorial!