IPv6 Security: Overview
Sumber: https://resources.infosecinstitute.com/topic/ipv6-security-overview-a-small-view-of-the-future/
Untuk sudut pandang yang benar, wajar untuk mempertimbangkan bahwa IPv6 tidak selalu lebih aman daripada IPv4. Pendekatan keamanan yang diterapkan, meskipun diterapkan secara signifikan, masih marjinal dan tidak sepenuhnya baru. Namun, ada beberapa pertimbangan yang, tanpa diragukan lagi, meningkatkan tingkat keandalan IPv6.
Wajib menggunakan IPSec
IPv4 juga menawarkan dukungan IPSec. Namun, dukungan untuk IPSec di IPv4 bersifat opsional. RFC4301 malah membuatnya wajib untuk digunakan di IPv6. IPSec terdiri dari sekumpulan protokol kriptografi yang dirancang untuk menyediakan keamanan dalam komunikasi data. IPSec memiliki beberapa protokol yang merupakan bagian dari rangkaiannya: AH (Authentication Header) dan ESP (Encapsulating Security Payload). Yang pertama menyediakan otentikasi dan integritas data, yang kedua, selain itu, juga untuk kerahasiaan. Di IPv6, header AH dan header ESP didefinisikan sebagai header ekstensi.
Konsep dasar IPSec adalah “Security Association” (SA). SA diidentifikasi secara unik oleh beberapa parameter seperti SPI (Security Parameters Index – kolom di header AH/ESP), protokol keamanan, dan alamat IP tujuan. SA menentukan jenis layanan keamanan untuk koneksi dan biasanya berisi kunci untuk enkripsi data serta algoritme enkripsi yang akan digunakan. IKE (Internet Key Exchange) adalah proses yang digunakan untuk menegosiasikan parameter yang diperlukan untuk membuat SA baru. Berikut adalah beberapa detail tentang AH dan ESP:
AH (Authentication Header):
As already said, AH provides for authentication and data integrity for the entire IPv6 packet. “Authentication” means that if an endpoint receives a packet with a specific source address, it can be assured that the IP packet did indeed come from that IP address.
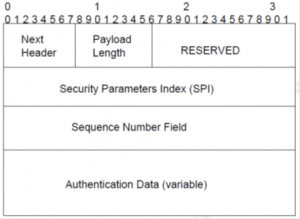
“Integrity,” on the other hand, means that if an endpoint receives data, the content of that data has not been modified along the path from the source to the destination. The figure below shows the format for AH:
AH (Header Autentikasi):
Seperti yang telah dikatakan, AH menyediakan otentikasi dan integritas data untuk seluruh paket IPv6. "Otentikasi" berarti bahwa jika titik akhir menerima paket dengan alamat sumber tertentu, dapat dipastikan bahwa paket IP memang berasal dari alamat IP tersebut.
"Integritas", di sisi lain, berarti bahwa jika titik akhir menerima data, konten data tersebut tidak diubah sepanjang jalur dari sumber ke tujuan. Gambar di bawah menunjukkan format AH:
From the image just shown, we can see some different fields. “Next Header” field identifies the transport type, like TCP. The “Payload Length” identifies the length of Authentication Header. The SPI field identifies the security parameter index which will be used to identifying the SA. The “Sequence Number Field” is a counter that increments by 1 when a sender or receiver receives or transmits data. Through SNF, an anti-replay protection is provided, because when the receiver receives a packet with a duplicate Sequence Number Field, this is discarded (we can see at “Session Replay” attacks in IPv4).
The “Authentication Data” contains the ICV (Integrity Check Value) which provides for data integrity and authentication. The ICV is calculated using the IP header, the IP packet payload and AH header. What happens in reality is that when the receiver receives the packet, it calculates the ICV with the algorithm and the specified key in SA. According with the details shown and the technology used, AH can prevent “IP Spoofing Attack”.
ESP (Encapsulating Security Payload):
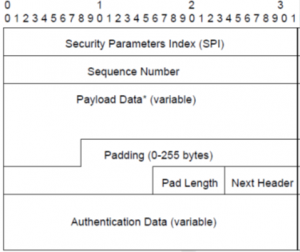
The ESP provides confidentiality, authentication and data integrity. With the term “confidentiality”, we mean that no one else, even the intended receiver, can read the content of communication in transit. As already mentioned for the AH, ESP also provides an anti-replay protection. The image below shows the format of an ESP packet:
As for the AH, ESP also contains an SPI field that is used to identify the SA. The “Sequence Number” field, as in the AH, provides an anti-replay protection. Interesting to note is the “Next Header” filed, which describes the data type contained in the “Payload Data” field (the entire packet if ESP is used in Tunnel Mode or only payload if is used in Transport Mode). The “Authentication Data” field contains the ICV (if auth service is specified by SA associated with SPI), which provides for authentication and data integrity. The authentication algorithm used to calculate the ICV is also specified by the SA.
2) Large Addressing Space:
As mentioned above, in IPv4, reconnaissance attacks and port scanning are relatively simple tasks. The most common network segments in the current Internet Protocol are of class C, with 8 bits allocated for addressing. Currently, performing this type of attacks on these network segments does not require more than a few minutes. Allocating 64 bits for addressing (as expected in an IPv6 subnet) means performing a net scan of 2^64 (18446744073709551616) hosts. It is practically impossible.
3) Neighbor Discovery:
ND (Neighbor Discovery) is the mechanism used for router and prefix discovery. This is a network layer protocol, like IPv4 equivalents ARP and RARP. ND works very closely with address auto-configuration, which is the mechanism used by IPv6 nodes to acquire configuration information. Both ND and address auto-configuration contribute to make IPv6 more secure than its predecessor.
IPng vs old attacks In this section we will analyze some of the most popular cyber attacks in a perspective focused on the comparison and on the possible impact of these with the IPng.
1) Reconnaissance Attacks:
Reconnaissance attacks, in IPv6, are different for two major reasons: The first is that “Ports Scan” and/or “Ping Sweep” are much less effective in IPv6, because of, as already said, the vastness of the subnet into play. The second is that new multicast addresses in IPv6 will allow finding key systems in a network easier, like routers and some type of servers. In addition, the IPv6 network has a much closer relationship with ICMPv6 (compared to the IPv4 counterparty ICMP) which does not allow too aggressive filters on this protocol. For the rest, the techniques remain the same.
2) Over the Wall:
This class will discuss the type of attacks in which an adversary tries to exploit little restrictive filtering policies. Currently, we are used to developing access lists (ACLs) to restrict unauthorized access to the network we want to be protected by set specific policies on gateway devices in between the IPv4 endpoints. The need for access control is the same in IPv6 as in IPv4. In IPv6, the basic functions for mitigation of unauthorized access are the same. However, considering the significant differences between the headers of the two protocols, it is possible to imagine different ways to implement them.
3) Spoofing Attacks:
While L4 spoofing remains the same, due to the globally aggregated nature of IPv6, spoofing mitigation is expected to be easier to deploy. However the host part of the address is not protected. Layer 4 spoofing attacks are not changed, because L4 protocols do not change in IPv6 with regard to spoofing.
4) DDoS Attacks:
In IPv6, we cannot find the broadcast address. This means that all resulting amplification attacks, like smurf, will be stopped. IPv6 specifications forbid the generation of ICMPv6 packets in response to messages to IPv6 multicast destination address, a link-layer multicast address or a link-layer broadcast address. In general, through the adoption of the new standard, we should find an improvement in this regard.
5) Routing Attacks:
Routing attacks refer to activities that try to redirect traffic flow within a network. Currently, routing protocols are protected using cryptographic authentication (MD5 with Pre-Shared Key) between peers. This protection mechanism will not be changing with IPng. BGP has been updated to carry IPv6 routing information.
6) Malware:
There is no particular implementation in IPv6 which will allow changing the classical approach to malware. However, worms that use the internet to find vulnerable hosts may find difficulties in propagation due to the large address space.
7) Sniffing:
This is the classical attack that involves capturing data in transit across a network. IPv6 provides the technology for the prevention of these types of attacks with IPSec, but it does not simplify the problems for keys management. For this reason, this technique can still continue to be practiced.
8) L7 Attacks:
Here we refer to all those types of attacks performed at Layer 7 of the OSI model. Also considering a worldwide adoption of IPSec, this type of attacks will remain almost unchanged. Buffer Overflow, Web Applications Vulnerability, etc., cannot be stopped through the IPv6 adoption. There is also another consideration: if IPSec will be implemented as a standard for communication between endpoints, all devices such as IDS/IPS, firewalls and antivirus will only see encrypted traffic, promoting this type of attacks.
9) Man-in-the-Middle:
The IPv6 is subjected to the same security risks that we may encounter in a man-in-the-middle attack that affects the suite of IPSec protocols.
10) Flooding Attacks:
A flooding attack is a Denial of Service (DoS) attack wherein the attacker sends a slew of SYN requests to a target’s system in order to overwhelm the server and bring down the network / make it unresponsive to actual traffic. So, in short, it’s exactly what it sounds like. The core principles of a flooding attack remain the same in IPv6.