GnuPG Privacy Handbook
Copyright © 1999 by The Free Software Foundation
Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.1 or any later version published by the Free Software Foundation; with no Invariant Sections, no Front-Cover Texts, and no Back-Cover Texts. A copy of the license is included in the section entitled "GNU Free Documentation License".
Please direct questions, bug reports, or suggestions concerning this manual to the maintainer, Mike Ashley (<jashley@acm.org>). When referring to the manual please specify which version of the manual you have by using this version string: $Name: v1_1 $.
Contributors to this manual include Matthew Copeland, Joergen Grahn, and David A. Wheeler. J Horacio MG has translated the manual to Spanish.
Chapter 1. Getting Started
GnuPG adalah alat komunikasi yang aman. Bab ini merupakan panduan ringkas yang mencakup fungsi inti GnuPG. Ini termasuk penciptaan keypair, pertukaran dan verifikasi kunci, mengenkripsi dan mendekripsi dokumen, dan mengautentikasi dokumen dengan tanda tangan digital. Ini tidak menjelaskan secara rinci konsep di balik kriptografi kunci publik, enkripsi, dan tanda tangan digital. Hal tersebut tercakup dalam Bab 2. Ini juga tidak menjelaskan bagaimana menggunakan GnuPG dengan bijak. Hal ini tercakup dalam Bab 3 dan 4.
GnuPG menggunakan kriptografi kunci publik sehingga pengguna dapat berkomunikasi dengan aman. Dalam sistem kunci publik, setiap pengguna memiliki sepasang kunci yang terdiri dari kunci pribadi dan kunci publik. Kunci pribadi pengguna dirahasiakan; Tidak perlu diungkap. Kunci publik dapat diberikan kepada siapa saja yang ingin berkomunikasi dengan pengguna. GnuPG menggunakan skema yang agak lebih canggih di mana pengguna memiliki keypair utama dan kemudian nol atau lebih tambahan keokohan bawahan. Keypairs utama dan bawahan digabungkan untuk memudahkan manajemen kunci dan bundel seringkali dianggap hanya sebagai satu keypair.
Membuat keypair baru
Opsi command line --gen-key digunakan untuk membuat primary keypair baru.
gpg --gen-key
gpg (GnuPG) 0.9.4; Copyright (C) 1999 Free Software Foundation, Inc. This program comes with ABSOLUTELY NO WARRANTY. This is free software, and you are welcome to redistribute it under certain conditions. See the file COPYING for details. Please select what kind of key you want: (1) DSA and ElGamal (default) (2) DSA (sign only) (4) ElGamal (sign and encrypt) Your selection?
GnuPG is able to create several different types of keypairs, but a primary key must be capable of making signatures. There are therefore only three options. Option 1 actually creates two keypairs. A DSA keypair is the primary keypair usable only for making signatures. An ElGamal subordinate keypair is also created for encr yption. Option 2 is similar but creates only a DSA keypair. Option 4[1] creates a single ElGamal keypair usable for both making signatures and performing encryption. In all cases it is possible to later add additional subkeys for encryption and signing. For most users the default option is fine.
Anda juga harus memilih panjang kunci. Panjang kunci DSA harus antara 512 dan 1024 bit, dan kunci ElGamal memungkinkan untuk panjang yang bebas. GnuPG, bagaimanapun, mensyaratkan bahwa kunci tidak lebih kecil dari 768 bit. Oleh karena itu, jika opsi 1 dipilih dan anda memilih ukuran kunci yang lebih besar dari 1024 bit, kunci ElGamal akan memiliki ukuran yang diminta, namun tombol DSA akan menjadi 1024 bit.
About to generate a new ELG-E keypair.
minimum keysize is 768 bits
default keysize is 1024 bits
highest suggested keysize is 2048 bits
What keysize do you want? (1024)
Semakin panjang kunci semakin aman terhadap serangan brute force, namun untuk hampir semua kebutuhan, ukuran kunci default sudah memadai karena akan lebih murah untuk menghindari enkripsi daripada mencoba memecahnya. Juga, enkripsi dan dekripsi akan lebih lambat karena ukuran kunci meningkat, dan ukuran kunci yang lebih besar dapat mempengaruhi panjang tanda tangan. Setelah dipilih, keysize tidak akan pernah bisa diubah.
Akhirnya, anda harus memilih tanggal kedaluwarsa. Jika opsi 1 dipilih, tanggal kedaluwarsa akan digunakan baik untuk ElGamal dan DSA keypair.
Please specify how long the key should be valid.
0 = key does not expire
<n> = key expires in n days
<n>w = key expires in n weeks
<n>m = key expires in n months
<n>y = key expires in n years
Key is valid for? (0)
Bagi sebagian besar pengguna, kunci yang tidak kedaluwarsa cukup memadai. Waktu kedaluwarsa harus dipilih dengan hati-hati, namun walaupun memungkinkan untuk mengubah tanggal kedaluwarsa setelah kunci dibuat, mungkin sulit untuk mengkomunikasikan perubahan pada pengguna yang memiliki kunci publik Anda.
Anda harus memberikan ID pengguna di samping parameter utama. ID pengguna digunakan untuk mengaitkan kunci yang dibuat dengan orang sesungguhnya.
You need a User-ID to identify your key; the software constructs the user id from Real Name, Comment and Email Address in this form:
"Heinrich Heine (Der Dichter) <heinrichh@duesseldorf.de>" Real name:
Hanya satu ID pengguna yang dibuat saat kunci dibuat, namun memungkinkan untuk membuat ID pengguna tambahan jika anda ingin menggunakan kunci tersebut dalam dua atau lebih konteks, misalnya, sebagai karyawan di tempat kerja dan aktivis politik di tempat lain. ID pengguna harus dibuat dengan hati-hati karena tidak dapat diedit setelah dibuat.
GnuPG membutuhkan frasa sandi untuk melindungi kunci privat utama dan bawahan yang anda simpan dalam kepemilikan anda.
You need a Passphrase to protect your private key. Enter passphrase:
Tidak ada batas panjang frasa sandi, dan harus dipilih dengan cermat. Dari sudut pandang keamanan, frasa sandi untuk membuka kunci pribadi adalah salah satu poin terlemah di GnuPG (dan sistem enkripsi kunci publik lainnya juga) karena ini adalah satu-satunya perlindungan yang anda miliki jika orang lain mendapatkan kunci pribadi anda. Idealnya, frasa sandi tidak boleh menggunakan kata-kata dari kamus dan harus mencampur kasus karakter alfabet serta menggunakan karakter non-abjad. Frasa sandi yang baik sangat penting untuk penggunaan GnuPG yang aman.
Membuat revocation certificate
Setelah keypair anda dibuat, anda harus segera membuat sertifikat pencabutan untuk kunci publik utama menggunakan opsi --gen-revoke. Jika anda lupa frasa sandi anda atau jika kunci pribadi anda dikompromikan atau hilang, sertifikat pencabutan ini dapat dipublikasikan untuk memberi tahu orang lain bahwa kunci publik seharusnya tidak lagi digunakan. Kunci publik yang dicabut masih dapat digunakan untuk memverifikasi tanda tangan yang dibuat oleh anda di masa lalu, namun tidak dapat digunakan untuk mengenkripsi pesan mendatang kepada anda. Ini juga tidak mempengaruhi kemampuan Anda untuk mendekripsi pesan yang dikirim kepada anda di masa lalu jika Anda masih memiliki akses ke kunci pribadi.
gpg --output revoke.asc --gen-revoke mykey [...]
Argumen mykey harus menjadi specifier kunci, baik ID kunci dari keypair utama anda atau bagian dari ID pengguna yang mengidentifikasi keypair anda. Sertifikat yang dihasilkan akan berada di file revoke.asc. Jika opsi --output dihilangkan, hasilnya akan ditempatkan pada output standar. Karena sertifikatnya pendek, anda mungkin ingin mencetak salinan sertifikat untuk menyimpan tempat yang aman seperti safe deposit box anda. Sertifikat tidak boleh disimpan di tempat dimana orang lain dapat mengaksesnya karena setiap orang dapat menerbitkan sertifikat pencabutan dan membuat kunci publik yang benar menjadi tidak berguna.
Mempertukarkan keys
Untuk berkomunikasi dengan orang lain anda harus bertukar kunci publik. Untuk melihat daftar key pada keyring publik anda dapat menggunakan opsi --list-keys.
alice% gpg --list-keys
/users/alice/.gnupg/pubring.gpg --------------------------------------- pub 1024D/BB7576AC 1999-06-04 Alice (Judge) <alice@cyb.org> sub 1024g/78E9A8FA 1999-06-04
Export public key
Untuk mengirim kunci publik anda ke koresponden anda harus terlebih dahulu mengekspornya. Opsi --export digunakan untuk melakukan ini. Dibutuhkan argumen tambahan untuk mengidentifikasi kunci publik untuk diekspor. Seperti opsi --gen-revoke, ID kunci atau bagian ID pengguna dapat digunakan untuk mengidentifikasi kunci yang akan diekspor.
alice% gpg --output alice.gpg --export alice@cyb.org
Kuncinya diekspor dalam format biner, tapi ini bisa merepotkan saat kuncinya dikirim meski email atau dipublikasikan di halaman web. Oleh karena itu, GnuPG mendukung opsi --armour yang menyebabkan keluaran dihasilkan dalam format ASCII-armoured yang serupa dengan dokumen yang di uuencoded. Secara umum, setiap keluaran dari GnuPG, mis., kunci, dokumen terenkripsi, dan tanda tangan, dapat menjadi ASCII-armoured dengan menambahkan opsi --armor.
alice% gpg --armor --export alice@cyb.org -----BEGIN PGP PUBLIC KEY BLOCK----- Version: GnuPG v0.9.7 (GNU/Linux) Comment: For info see http://www.gnupg.org [...] -----END PGP PUBLIC KEY BLOCK-----
Importing a public key
sebuah public key dapat di tambahkan pada public keyring anda dengan opsi --import
gpg --import blake.gpg
gpg: key 9E98BC16: public key imported gpg: Total number processed: 1 gpg: imported: 1
gpg --list-keys
/users/alice/.gnupg/pubring.gpg --------------------------------------- pub 1024D/BB7576AC 1999-06-04 Alice (Judge) <alice@cyb.org> sub 1024g/78E9A8FA 1999-06-04 pub 1024D/9E98BC16 1999-06-04 Blake (Executioner) <blake@cyb.org> sub 1024g/5C8CBD41 1999-06-04
Sekali kunci diimpor itu harus divalidasi. GnuPG menggunakan model kepercayaan yang kuat dan fleksibel yang tidak mengharuskan anda untuk secara pribadi memvalidasi setiap kunci yang anda impor. Beberapa kunci mungkin perlu divalidasi secara pribadi. Kunci divalidasi dengan memverifikasi fingerprint kunci dan kemudian menandatangani kunci untuk menyatakannya sebagai kunci yang valid. Fingerprint kunci dapat dilihat dengan cepat dengan opsi --fingerprint, namun untuk mengesahkan kunci, anda harus mengeditnya.
gpg --edit-key blake@cyb.org pub 1024D/9E98BC16 created: 1999-06-04 expires: never trust: -/q sub 1024g/5C8CBD41 created: 1999-06-04 expires: never (1) Blake (Executioner) <blake@cyb.org>
Command> fpr
pub 1024D/9E98BC16 1999-06-04 Blake (Executioner) <blake@cyb.org>
Fingerprint: 268F 448F CCD7 AF34 183E 52D8 9BDE 1A08 9E98 BC16
Fingerprint kunci diverifikasi dengan pemilik kunci. Hal ini dapat dilakukan secara langsung atau melalui telepon atau melalui cara lain selama anda dapat menjamin bahwa anda berkomunikasi dengan pemilik kunci yang sebenarnya. Jika fingerprint yang anda dapatkan sama dengan fingerprint pemilik kunci, anda dapat yakin bahwa anda memiliki salinan kunci yang benar.
Setelah memeriksa fingerprint, anda dapat menandatangani kunci untuk memvalidasinya. Karena verifikasi kunci adalah titik lemah dalam kriptografi kunci publik, anda harus sangat berhati-hati dan selalu memeriksa sidik jari kunci dengan pemiliknya sebelum menandatangani kunci.
Command> sign
pub 1024D/9E98BC16 created: 1999-06-04 expires: never trust: -/q
Fingerprint: 268F 448F CCD7 AF34 183E 52D8 9BDE 1A08 9E98 BC16
Blake (Executioner) <blake@cyb.org>
Are you really sure that you want to sign this key
with your key: "Alice (Judge) <alice@cyb.org>"
Really sign?
Setelah masuk, anda dapat memeriksa kunci untuk mencantumkan signature di atasnya dan melihat signature yang telah anda tambahkan. Setiap ID pengguna di kunci akan memiliki satu atau lebih signature sendiri dan juga signature untuk setiap pengguna yang telah memvalidasi kuncinya.
Command> check uid Blake (Executioner) <blake@cyb.org> sig! 9E98BC16 1999-06-04 [self-signature] sig! BB7576AC 1999-06-04 Alice (Judge) <alice@cyb.org>
Enkripsi dan dekripsi dokumen
Kunci publik dan kunci private masing-masing memiliki peran khusus saat mengenkripsi dan mendekripsi dokumen. Kunci publik dapat dianggap sebagai brankas terbuka. Ketika seorang koresponden mengenkripsi dokumen dengan menggunakan kunci publik, dokumen itu dimasukkan ke dalam brankas, brankas ditutup, dan kunci kombinasi diputar beberapa kali. Kunci pribadi yang sesuai adalah kombinasi yang dapat membuka kembali brankas dan mengambil dokumen. Dengan kata lain, hanya orang yang memegang kunci privat dapat mengembalikan dokumen yang dienkripsi menggunakan kunci publik yang terkait.
Prosedur untuk mengenkripsi dan mendekripsi dokumen sangat mudah dengan model mental ini. Jika Anda ingin mengenkripsi pesan ke Alice, Anda mengenkripsi dengan menggunakan kunci publik Alice, dan dia mendekrip dengan kunci private-nya. Jika Alice ingin mengirimi anda pesan, dia mengenkripsinya menggunakan kunci publik anda, dan anda mendekripnya dengan kunci private anda.
Untuk mengenkripsi sebuah dokumen gunakan opsi --encrypt . Anda harus memiliki kunci publik dari penerima yang dimaksud. Perangkat lunak mengharapkan nama dokumen untuk dienkripsi sebagai masukan; Jika dihilangkan, ia membaca input standar. Hasil terenkripsi ditempatkan pada keluaran standar atau sesuai dengan opsi --output. Dokumen ini dikompres untuk keamanan tambahan selain mengenkripsi.
alice% gpg --output doc.gpg --encrypt --recipient blake@cyb.org doc
Opsi --recipient digunakan satu kali untuk setiap penerima dan mengambil argumen tambahan yang menentukan kunci publik yang dokumennya harus dienkripsi. Dokumen terenkripsi hanya bisa didekripsi oleh seseorang dengan kunci pribadi yang melengkapi salah satu kunci publik penerima. Secara khusus, anda tidak dapat mendekripsi sebuah dokumen yang dienkripsi oleh anda kecuali anda menyertakan kunci publik anda sendiri dalam daftar penerima.
Untuk mendekrip pesan gunakan opsi --decrypt . Anda memerlukan kunci privat yang digunakan untuk meng-enkripsi pesan. Serupa dengan proses enkripsi, dokumen yang akan didekrip adalah input, dan hasil dekrip adalah output.
blake% gpg --output doc --decrypt doc.gpg You need a passphrase to unlock the secret key for user: "Blake (Executioner) <blake@cyb.org>" 1024-bit ELG-E key, ID 5C8CBD41, created 1999-06-04 (main key ID 9E98BC16) Enter passphrase:
Dokumen juga dapat dienkripsi tanpa menggunakan kriptografi kunci publik. Sebagai gantinya, anda menggunakan cipher simetris untuk mengenkripsi dokumen. Kunci yang digunakan untuk cipher simetris berasal dari frasa sandi yang diberikan saat dokumen dienkripsi, dan untuk keamanan yang baik, kunci tersebut tidak boleh sama dengan frasa sandi yang anda gunakan untuk melindungi kunci privat anda. Enkripsi simetris berguna untuk mengamankan dokumen bila frasa sandi tidak perlu dikomunikasikan kepada orang lain. Sebuah dokumen dapat dienkripsi dengan cipher simetris dengan menggunakan opsi --symmetric.
alice% gpg --output doc.gpg --symmetric doc Enter passphrase: Making and verifying signatures
Tanda tangan digital memberi tanda dan cap waktu sebuah dokumen. Jika dokumen kemudian diubah dengan cara apapun, verifikasi tanda tangan akan gagal. Tanda tangan digital dapat melayani tujuan yang sama seperti tanda tangan yang ditulis tangan dengan tambahan keuntungan karena tahan terhadap pengrusakan / perubahan. Distribusi sumber GnuPG, misalnya, ditandatangani sehingga pengguna dapat memverifikasi bahwa kode sumbernya belum dimodifikasi sejak dikemas.
Membuat dan memverifikasi tanda tangan menggunakan keypair publik / private dalam operasi yang berbeda dengan enkripsi dan dekripsi. Tanda tangan dibuat dengan menggunakan kunci pribadi penandatangan. Tanda tangan diverifikasi menggunakan kunci publik yang sesuai. Misalnya, Alice akan menggunakan kunci privat-nya untuk menandatangani secara digital kiriman terakhirnya ke Journal of Anorganic Chemistry. Editor asosiasi yang menangani pengirimannya akan menggunakan kunci publik Alice untuk memeriksa tanda tangan untuk memverifikasi bahwa penyerahannya benar-benar berasal dari Alice dan itu tidak dimodifikasi sejak Alice mengirimkannya. Konsekuensi menggunakan tanda tangan digital adalah sulit untuk menyangkal bahwa anda membuat tanda tangan digital karena itu berarti kunci pribadi anda telah disusupi.
Opsi --sign digunakan untuk membuat tanda tangan digital. Dokumen yang akan ditandatangani adalah input, dan dokumen yang ditandatangani adalah output.
alice% gpg --output doc.sig --sign doc You need a passphrase to unlock the private key for user: "Alice (Judge) <alice@cyb.org>" 1024-bit DSA key, ID BB7576AC, created 1999-06-04 Enter passphrase:
Dokumen dikompres sebelum ditandatangani, dan hasilnya ada dalam format biner.
Dengan dokumen yang ditandatangani, anda bisa mengecek tanda tangan atau memeriksa tanda tangan dan mengembalikan dokumen aslinya. Untuk mengecek tanda tangan gunakan opsi --verify. Untuk memverifikasi tanda tangan dan ekstrak dokumen gunakan opsi --decrypt. Dokumen yang ditandatangani untuk memverifikasi dan memulihkan adalah masukan dan dokumen yang dipulihkan adalah keluaran.
blake% gpg --output doc --decrypt doc.sig gpg: Signature made Fri Jun 4 12:02:38 1999 CDT using DSA key ID BB7576AC gpg: Good signature from "Alice (Judge) <alice@cyb.org>"
Clearsigned dokumen
Penggunaan tanda tangan digital yang umum adalah menandatangani posting atau pesan email usenet. Dalam situasi seperti itu, tidak diinginkan untuk mengkompres dokumen saat menandatanganinya. Opsi --clearsign menyebabkan dokumen dibungkus dengan tanda tangan ASCII-armoured namun tidak mengubah dokumen.
alice% gpg --clearsign doc
You need a passphrase to unlock the secret key for user: "Alice (Judge) <alice@cyb.org>" 1024-bit DSA key, ID BB7576AC, created 1999-06-04 -----BEGIN PGP SIGNED MESSAGE----- Hash: SHA1 [...] -----BEGIN PGP SIGNATURE----- Version: GnuPG v0.9.7 (GNU/Linux) Comment: For info see http://www.gnupg.org iEYEARECAAYFAjdYCQoACgkQJ9S6ULt1dqz6IwCfQ7wP6i/i8HhbcOSKF4ELyQB1 oCoAoOuqpRqEzr4kOkQqHRLE/b8/Rw2k =y6kj -----END PGP SIGNATURE-----
Detached signatures
Dokumen yang ditandatangani memiliki kegunaan yang terbatas. Pengguna lain harus memulihkan dokumen asli dari versi yang ditandatangani, dan bahkan dengan dokumen yang jelas, dokumen yang ditandatangani harus diedit untuk memulihkan dokumen asli. Oleh karena itu, ada metode ketiga untuk menandatangani dokumen yang membuat tanda tangan terpisah, yang merupakan file terpisah. Tanda tangan terpisah dibuat menggunakan opsi --detach-sig.
gpg --output doc.sig --detach-sig doc
You need a passphrase to unlock the secret key for user: "Alice (Judge) <alice@cyb.org>" 1024-bit DSA key, ID BB7576AC, created 1999-06-04 Enter passphrase:
Baik dokumen maupun tanda tangan yang diperlukan untuk mendapatkan tanda tangan. Untuk mengecek signature bisa menggunakan opsi --verify ;.
gpg --verify doc.sig doc
gpg: Signature made Fri Jun 4 12:38:46 1999 CDT using DSA key ID BB7576AC gpg: Good signature from "Alice (Judge) <alice@cyb.org>"
Chapter 2. Konsep
GnuPG memanfaatkan beberapa konsep kriptografi termasuk cipher simetris, cipher kunci publik, dan hashing satu arah. Anda bisa membuat penggunaan dasar GnuPG tanpa memahami sepenuhnya konsep ini, namun untuk menggunakannya dengan bijak, beberapa pemahaman tentang hal itu diperlukan.
Bab ini memperkenalkan konsep kriptografi dasar yang digunakan dalam GnuPG. Buku-buku lain mencakup topik-topik ini secara lebih rinci. Sebuah buku bagus untuk dipelajari selanjutnya adalah "Applied Cryptography" oleh Bruce Schneier.
Symmetric cipher
Cipher simetris adalah cipher yang menggunakan kunci yang sama untuk enkripsi dan dekripsi. Dua pihak yang berkomunikasi menggunakan cipher simetris harus menyetujui kunci sebelumnya. Begitu mereka setuju, pengirim mengenkripsi pesan menggunakan kunci tersebut, mengirimkannya ke penerima, dan penerima mendekripsi pesan menggunakan kunci tersebut. Sebagai contoh, Enigma Jerman adalah cipher simetris, dan kunci harian didistribusikan sebagai buku kode. Setiap hari, operator radio pengirim atau penerima akan berkonsultasi dengan fotokopi buku kode untuk menemukan kunci hari itu. Lalu lintas radio untuk hari itu kemudian dienkripsi dan didekripsi dengan menggunakan kunci hari itu. Contoh modern dari simetris cipher meliputi 3DES, Blowfish, dan IDEA.
Sebuah cipher yang baik menempatkan semua keamanan pada key dan tidak ada dalam algoritma. Dengan kata lain, seharusnya tidak ada gunanya bagi penyerang jika dia mengetahui cipher mana yang sedang digunakan. Hanya jika dia mendapatkan kunci pengetahuan tentang algoritma dibutuhkan. Cipher yang digunakan di GnuPG memiliki properti ini.
Karena semua keamanan ada di kunci, penting sekali untuk mempersulit menebak kuncinya. Dengan kata lain, set kunci yang mungkin, yaitu, panjang kunci, harus berukuran besar. Sementara di Los Alamos, Richard Feynman terkenal karena kemampuannya untuk menjebol lemari besi. Untuk mendorong mistik ia bahkan membawa kemana-mana seperangkat alat termasuk stetoskop tua. Pada kenyataannya, ia menggunakan berbagai trik untuk mengurangi jumlah kombinasi yang ia coba untuk sejumlah kecil dan kemudian bisa ditebak sampai ia menemukan kombinasi yang tepat. Dengan kata lain, ia mengurangi ukuran panjang kunci.
Inggris menggunakan mesin untuk menebak kunci selama Perang Dunia 2. Enigma Jerman memiliki panjang kunci yang sangat besar, namun Inggris membangun mesin penghitung khusus, Bombes, untuk secara mekanis mencoba kunci sampai kunci hari itu ditemukan. Ini berarti kadang kala mereka menemukan kunci hari itu dalam hitungan jam penggunaan kunci baru, tapi itu juga berarti bahwa pada beberapa hari mereka tidak pernah menemukan kunci yang tepat. Bombes bukanlah komputer dengan tujuan umum namun merupakan prekursor komputer modern.
Saat ini, komputer bisa menebak kunci dengan sangat cepat, dan inilah sebabnya ukuran kunci penting dalam kriptosistem modern. DES cipher menggunakan kunci 56-bit, yang berarti ada 256 kemungkinan kunci. 256 adalah 72.057.594.037.927.936 kunci. Ini adalah kunci yang panjang, namun komputer tujuan umum dapat memeriksa keseluruhan panjang kunci dalam hitungan hari. Komputer khusus bisa memeriksanya berjam-jam. Di sisi lain, cipher yang baru dirancang seperti 3DES, Blowfish, dan IDEA semua menggunakan kunci 128-bit, yang berarti ada 2128 kemungkinan kunci. Ini kunci yang jauh lebih panjang lagi, dan bahkan jika semua komputer di planet ini bekerja sama, masih bisa memakan waktu lebih lama dari pada usia alam semesta untuk menemukan kuncinya.
Public-key cipher
Masalah utama dengan simetris cipher bukan keamanan mereka tapi dengan pertukaran kunci. Begitu pengirim dan penerima saling bertukar kunci, kunci itu bisa digunakan untuk berkomunikasi dengan aman, tapi saluran komunikasi aman mana yang digunakan untuk mengkomunikasikan kunci itu sendiri? Secara khusus, mungkin akan lebih mudah bagi penyerang untuk mencoba mencegat kunci daripada mencoba semua kemungkinan kunci. Masalah lainnya adalah banyaknya kunci yang dibutuhkan. Jika ada n orang yang perlu berkomunikasi, maka di perlukan n(n-1)/2 kunci untuk setiap pasangan orang untuk berkomunikasi secara pribadi. Ini mungkin baik untuk sejumlah kecil orang tapi dengan cepat menjadi berat bagi kelompok besar orang.
Cipher kunci publik diciptakan untuk menghindari masalah pertukaran kunci sepenuhnya. Cipher kunci publik menggunakan sepasang kunci untuk mengirim pesan. Kedua kunci itu milik orang yang menerima pesan tersebut. Salah satu kunci adalah kunci publik dan mungkin diberikan kepada siapa saja. Kunci lainnya adalah kunci private dan dirahasiakan oleh pemiliknya. Pengirim mengenkripsi pesan menggunakan kunci publik dan saat dienkrip, hanya kunci private yang dapat digunakan untuk mendekrip-nya.
Protokol ini memecahkan masalah pertukaran kunci yang melekat pada simetris cipher. Tidak perlu bagi pengirim dan penerima untuk menyetujui sebuah kunci. Yang dibutuhkan hanyalah beberapa saat sebelum komunikasi rahasia pengirim mendapat salinan kunci publik penerima. Selanjutnya, satu kunci publik dapat digunakan oleh siapa saja yang ingin berkomunikasi dengan penerima. Jadi, hanya n keypairs yang dibutuhkan n untuk saling berkomunikasi satu sama lain.
Kunci publik ciphers didasarkan pada fungsi one-way trapdoor. Fungsi satu arah adalah fungsi yang mudah dihitung, namun inversnya sulit dihitung. Sebagai contoh, mudah untuk mengalikan dua bilangan prima bersama-sama untuk mendapatkan komposit, namun sulit untuk menentukan komposit menjadi komponen utamanya. Fungsi one-way trapdoor serupa, namun memiliki pintu jebakan. Artinya, jika beberapa informasi diketahui, maka menjadi mudah untuk menghitung invers. Misalnya, jika anda memiliki nomor yang terdiri dari dua faktor prima, maka mengetahui salah satu faktor memudahkan untuk menghitung yang kedua. Dengan menggunakan cipher kunci publik berdasarkan faktorisasi prima, kunci publik berisi bilangan komposit yang dibuat dari dua faktor prima yang besar, dan algoritma enkripsi menggunakan komposit tersebut untuk mengenkripsi pesan. Algoritma untuk mendekripsi pesan memerlukan mengetahui faktor prima, jadi dekripsi mudah dilakukan jika anda memiliki kunci pribadi yang berisi salah satu faktor namun sangat sulit jika anda tidak memilikinya.
Seperti halnya dengan cipher simetris yang baik, dengan kunci publik yang bagus, semua keamanan bersandar pada kuncinya. Oleh karena itu, ukuran kunci adalah ukuran keamanan sistem, namun tidak dapat membandingkan ukuran kunci cipher simetris dan kunci sandi kunci publik sebagai ukuran keamanan relatif mereka. Dalam serangan brute force pada cipher simetris dengan ukuran kunci 80 bit, penyerang harus menghitung hingga 280 kunci untuk menemukan kunci yang tepat. Dalam serangan brute force pada kunci publik kunci dengan ukuran kunci 512 bit, penyerang harus memasukkan bilangan komposit yang dikodekan dalam 512 bit (sampai 155 digit desimal). Beban kerja penyerang pada dasarnya berbeda tergantung pada cipher yang sedang diserangnya. Sementara 128 bit cukup untuk simetris ciphers, mengingat hari ini teknologi kunci publik dengan 1024 bit yang direkomendasikan untuk sebagian besar tujuan.
Hybrid cipher
Cipher kunci publik bukanlah obat mujarab. Banyak ciphers simetris lebih kuat dari sudut pandang keamanan, dan enkripsi dan dekripsi kunci publik lebih mahal daripada operasi yang sesuai pada sistem simetris. Cipher kunci publik tetap merupakan alat yang efektif untuk mendistribusikan kunci cipher simetris, dan begitulah cara penggunaannya dalam sistem cipher hibrida.
Cipher hibrida menggunakan cipher simetris dan cipher kunci publik. Ia bekerja dengan menggunakan cipher kunci publik untuk berbagi kunci untuk cipher simetris. Pesan sebenarnya yang dikirim kemudian dienkripsi menggunakan kunci dan dikirim ke penerima. Karena pembagian kunci simetris aman, kunci simetris yang digunakan berbeda untuk setiap pesan yang dikirim. Oleh karena itu terkadang disebut session key.
Baik PGP dan GnuPG menggunakan teknologi hybrid ciphers. Key session, dienkripsi menggunakan kunci publik, dan pesan yang dikirim, yang dienkripsi dengan cipher simetris, digabungkan secara otomatis dalam satu paket. Penerima menggunakan kunci pribadinya untuk mendekrip key session dan key session kemudian digunakan untuk mendekrip pesan.
A hybrid cipher is no stronger than the public-key cipher or symmetric cipher it uses, whichever is weaker. In PGP and GnuPG, the public-key cipher is probably the weaker of the pair. Fortunately, however, if an attacker could decrypt a session key it would only be useful for reading the one message encrypted with that session key. The attacker would have to start over and decrypt another session key in order to read any other message. Digital signatures
A hash function is a many-to-one function that maps its input to a value in a finite set. Typically this set is a range of natural numbers. A simple hash function is f(x) = 0 for all integers x. A more interesting hash function is f(x) = x mod 37, which maps x to the remainder of dividing x by 37.
A document's digital signature is the result of applying a hash function to the document. To be useful, however, the hash function needs to satisfy two important properties. First, it should be hard to find two documents that hash to the same value. Second, given a hash value it should be hard to recover the document that produced that value.
Some public-key ciphers[3] could be used to sign documents. The signer encrypts the document with his private key. Anybody wishing to check the signature and see the document simply uses the signer's public key to decrypt the document. This algorithm does satisfy the two properties needed from a good hash function, but in practice, this algorithm is too slow to be useful.
An alternative is to use hash functions designed to satisfy these two important properties. SHA and MD5 are examples of such algorithms. Using such an algorithm, a document is signed by hashing it, and the hash value is the signature. Another person can check the signature by also hashing their copy of the document and comparing the hash value they get with the hash value of the original document. If they match, it is almost certain that the documents are identical.
Of course, the problem now is using a hash function for digital signatures without permitting an attacker to interfere with signature checking. If the document and signature are sent unencrypted, an attacker could modify the document and generate a corresponding signature without the recipient's knowledge. If only the document is encrypted, an attacker could tamper with the signature and cause a signature check to fail. A third option is to use a hybrid public-key encryption to encrypt both the signature and document. The signer uses his private key, and anybody can use his public key to check the signature and document. This sounds good but is actually nonsense. If this algorithm truly secured the document it would also secure it from tampering and there would be no need for the signature. The more serious problem, however, is that this does not protect either the signature or document from tampering. With this algorithm, only the session key for the symmetric cipher is encrypted using the signer's private key. Anybody can use the public key to recover the session key. Therefore, it is straightforward for an attacker to recover the session key and use it to encrypt substitute documents and signatures to send to others in the sender's name.
An algorithm that does work is to use a public key algorithm to encrypt only the signature. In particular, the hash value is encrypted using the signer's private key, and anybody can check the signature using the public key. The signed document can be sent using any other encryption algorithm including none if it is a public document. If the document is modified the signature check will fail, but this is precisely what the signature check is supposed to catch. The Digital Signature Standard (DSA) is a public key signature algorithm that works as just described. DSA is the primary signing algorithm used in GnuPG.
Chapter 3. Key Management
Key tampering is a major security weakness with public-key cryptography. An eavesdropper may tamper with a user's keyrings or forge a user's public key and post it for others to download and use. For example, suppose Chloe wants to monitor the messages that Alice sends to Blake. She could mount what is called a man in the middle attack. In this attack, Chloe creates a new public/private keypair. She replaces Alice's copy of Blake's public key with the new public key. She then intercepts the messages that Alice sends to Blake. For each intercept, she decrypts it using the new private key, reencrypts it using Blake's true public key, and forwards the reencrypted message to Blake. All messages sent from Alice to Blake can now be read by Chloe.
Good key management is crucial in order to ensure not just the integrity of your keyrings but the integrity of other users' keyrings as well. The core of key management in GnuPG is the notion of signing keys. Key signing has two main purposes: it permits you to detect tampering on your keyring, and it allows you to certify that a key truly belongs to the person named by a user ID on the key. Key signatures are also used in a scheme known as the web of trust to extend certification to keys not directly signed by you but signed by others you trust. Responsible users who practice good key management can defeat key tampering as a practical attack on secure communication with GnuPG. Managing your own keypair
A keypair has a public key and a private key. A public key consists of the public portion of the master signing key, the public portions of the subordinate signing and encryption subkeys, and a set of user IDs used to associate the public key with a real person. Each piece has data about itself. For a key, this data includes its ID, when it was created, when it will expire, etc. For a user ID, this data includes the name of the real person it identifies, an optional comment, and an email address. The structure of the private key is similar, except that it contains only the private portions of the keys, and there is no user ID information.
The command-line option --edit-key may be used to view a keypair. For example,
chloe% gpg --edit-key chloe@cyb.org Secret key is available. pub 1024D/26B6AAE1 created: 1999-06-15 expires: never trust: -/u sub 2048g/0CF8CB7A created: 1999-06-15 expires: never sub 1792G/08224617 created: 1999-06-15 expires: 2002-06-14 sub 960D/B1F423E7 created: 1999-06-15 expires: 2002-06-14 (1) Chloe (Jester) <chloe@cyb.org> (2) Chloe (Plebian) <chloe@tel.net> Command>
The public key is displayed along with an indication of whether or not the private key is available. Information about each component of the public key is then listed. The first column indicates the type of the key. The keyword pub identifies the public master signing key, and the keyword sub identifies a public subordinate key. The second column indicates the key's bit length, type, and ID. The type is D for a DSA key, g for an encryption-only ElGamal key, and G for an ElGamal key that may be used for both encryption and signing. The creation date and expiration date are given in columns three and four. The user IDs are listed following the keys.
More information about the key can be obtained with interactive commands. The command toggle switches between the public and private components of a keypair if indeed both components are available.
Command> toggle sec 1024D/26B6AAE1 created: 1999-06-15 expires: never sbb 2048g/0CF8CB7A created: 1999-06-15 expires: never sbb 1792G/08224617 created: 1999-06-15 expires: 2002-06-14 sbb 960D/B1F423E7 created: 1999-06-15 expires: 2002-06-14 (1) Chloe (Jester) <chloe@cyb.org> (2) Chloe (Plebian) <chloe@tel.net>
The information provided is similar to the listing for the public-key component. The keyword sec identifies the private master signing key, and the keyword sbb identifies the private subordinates keys. The user IDs from the public key are also listed for convenience.
Key integrity
When you distribute your public key, you are distributing the public components of your master and subordinate keys as well as the user IDs. Distributing this material alone, however, is a security risk since it is possible for an attacker to tamper with the key. The public key can be modified by adding or substituting keys, or by adding or changing user IDs. By tampering with a user ID, the attacker could change the user ID's email address to have email redirected to himself. By changing one of the encryption keys, the attacker would also be able to decrypt the messages redirected to him.
Using digital signatures is a solution to this problem. When data is signed by a private key, the corresponding public key is bound to the signed data. In other words, only the corresponding public key can be used to verify the signature and ensure that the data has not been modified. A public key can be protected from tampering by using its corresponding private master key to sign the public key components and user IDs, thus binding the components to the public master key. Signing public key components with the corresponding private master signing key is called self-signing, and a public key that has self-signed user IDs bound to it is called a certificate.
As an example, Chloe has two user IDs and three subkeys. The signatures on the user IDs can be checked with the command check from the key edit menu.
chloe% gpg --edit-key chloe Secret key is available. pub 1024D/26B6AAE1 created: 1999-06-15 expires: never trust: -/u sub 2048g/0CF8CB7A created: 1999-06-15 expires: never sub 1792G/08224617 created: 1999-06-15 expires: 2002-06-14 sub 960D/B1F423E7 created: 1999-06-15 expires: 2002-06-14 (1) Chloe (Jester) <chloe@cyb.org> (2) Chloe (Plebian) <chloe@tel.net> Command> check uid Chloe (Jester) <chloe@cyb.org> sig! 26B6AAE1 1999-06-15 [self-signature] uid Chloe (Plebian) <chloe@tel.net> sig! 26B6AAE1 1999-06-15 [self-signature]
As expected, the signing key for each signature is the master signing key with key ID 0x26B6AAE1. The self-signatures on the subkeys are present in the public key, but they are not shown by the GnuPG interface.
Adding and deleting key components
Both new subkeys and new user IDs may be added to your keypair after it has been created. A user ID is added using the command adduid. You are prompted for a real name, email address, and comment just as when you create an initial keypair. A subkey is added using the command addkey. The interface is similar to the interface used when creating an initial keypair. The subkey may be a DSA signing key, and encrypt-only ElGamal key, or a sign-and-encrypt ElGamal key. When a subkey or user ID is generated it is self-signed using your master signing key, which is why you must supply your passphrase when the key is generated.
Additional user IDs are useful when you need multiple identities. For example, you may have an identity for your job and an identity for your work as a political activist. Coworkers will know you by your work user ID. Coactivists will know you by your activist user ID. Since those groups of people may not overlap, though, each group may not trust the other user ID. Both user IDs are therefore necessary.
Additional subkeys are also useful. The user IDs associated with your public master key are validated by the people with whom you communicate, and changing the master key therefore requires recertification. This may be difficult and time consuming if you communicate with many people. On the other hand, it is good to periodically change encryption subkeys. If a key is broken, all the data encrypted with that key will be vulnerable. By changing keys, however, only the data encrypted with the one broken key will be revealed.
Subkeys and user IDs may also be deleted. To delete a subkey or user ID you must first select it using the key or uid commands respectively. These commands are toggles. For example, the command key 2 selects the second subkey, and invoking key 2 again deselects it. If no extra argument is given, all subkeys or user IDs are deselected. Once the user IDs to be deleted are selected, the command deluid actually deletes the user IDs from your key. Similarly, the command delkey deletes all selected subkeys from both your public and private keys.
For local keyring management, deleting key components is a good way to trim other people's public keys of unnecessary material. Deleting user IDs and subkeys on your own key, however, is not always wise since it complicates key distribution. By default, when a user imports your updated public key it will be merged with the old copy of your public key on his ring if it exists. The components from both keys are combined in the merge, and this effectively restores any components you deleted. To properly update the key, the user must first delete the old version of your key and then import the new version. This puts an extra burden on the people with whom you communicate. Furthermore, if you send your key to a keyserver, the merge will happen regardless, and anybody who downloads your key from a keyserver will never see your key with components deleted. Consequently, for updating your own key it is better to revoke key components instead of deleting them.
Revoking key components
To revoke a subkey it must be selected. Once selected it may be revoked with the revkey command. The key is revoked by adding a revocation self-signature to the key. Unlike the command-line option --gen-revoke, the effect of revoking a subkey is immediate.
Command> revkey Do you really want to revoke this key? y You need a passphrase to unlock the secret key for user: "Chloe (Jester) <chloe@cyb.org>" 1024-bit DSA key, ID B87DBA93, created 1999-06-28 pub 1024D/B87DBA93 created: 1999-06-28 expires: never trust: -/u sub 2048g/B7934539 created: 1999-06-28 expires: never sub 1792G/4E3160AD created: 1999-06-29 expires: 2000-06-28 rev! subkey has been revoked: 1999-06-29 sub 960D/E1F56448 created: 1999-06-29 expires: 2000-06-28 (1) Chloe (Jester) <chloe@cyb.org> (2) Chloe (Plebian) <chloe@tel.net>
A user ID is revoked differently. Normally, a user ID collects signatures that attest that the user ID describes the person who actually owns the associated key. In theory, a user ID describes a person forever, since that person will never change. In practice, though, elements of the user ID such as the email address and comment may change over time, thus invalidating the user ID.
The OpenPGP specification does not support user ID revocation, but a user ID can effectively be revoked by revoking the self-signature on the user ID. For the security reasons described previously, correspondents will not trust a user ID with no valid self-signature.
A signature is revoked by using the command revsig. Since you may have signed any number of user IDs, the user interface prompts you to decide for each signature whether or not to revoke it.
Command> revsig
You have signed these user IDs:
Chloe (Jester) <chloe@cyb.org>
signed by B87DBA93 at 1999-06-28
Chloe (Plebian) <chloe@tel.net>
signed by B87DBA93 at 1999-06-28
user ID: "Chloe (Jester) <chloe@cyb.org>"
signed with your key B87DBA93 at 1999-06-28
Create a revocation certificate for this signature? (y/N)n
user ID: "Chloe (Plebian) <chloe@tel.net>"
signed with your key B87DBA93 at 1999-06-28
Create a revocation certificate for this signature? (y/N)y
You are about to revoke these signatures:
Chloe (Plebian) <chloe@tel.net>
signed by B87DBA93 at 1999-06-28
Really create the revocation certificates? (y/N)y
You need a passphrase to unlock the secret key for
user: "Chloe (Jester) <chloe@cyb.org>"
1024-bit DSA key, ID B87DBA93, created 1999-06-28
pub 1024D/B87DBA93 created: 1999-06-28 expires: never trust: -/u
sub 2048g/B7934539 created: 1999-06-28 expires: never
sub 1792G/4E3160AD created: 1999-06-29 expires: 2000-06-28
rev! subkey has been revoked: 1999-06-29
sub 960D/E1F56448 created: 1999-06-29 expires: 2000-06-28
(1) Chloe (Jester) <chloe@cyb.org>
(2) Chloe (Plebian) <chloe@tel.net>
A revoked user ID is indicated by the revocation signature on the ID when the signatures on the key's user IDs are listed.
Command> check uid Chloe (Jester) <chloe@cyb.org> sig! B87DBA93 1999-06-28 [self-signature] uid Chloe (Plebian) <chloe@tel.net> rev! B87DBA93 1999-06-29 [revocation] sig! B87DBA93 1999-06-28 [self-signature]
Revoking both subkeys and self-signatures on user IDs adds revocation self-signatures to the key. Since signatures are being added and no material is deleted, a revocation will always be visible to others when your updated public key is distributed and merged with older copies of it. Revocation therefore guarantees that everybody has a consistent copy of your public key. Updating a key's expiration time
The expiration time of a key may be updated with the command expire from the key edit menu. If no key is selected the expiration time of the primary key is updated. Otherwise the expiration time of the selected subordinate key is updated.
A key's expiration time is associated with the key's self-signature. The expiration time is updated by deleting the old self-signature and adding a new self-signature. Since correspondents will not have deleted the old self-signature, they will see an additional self-signature on the key when they update their copy of your key. The latest self-signature takes precedence, however, so all correspondents will unambiguously know the expiration times of your keys.
Validating other keys on your public keyring
In Chapter 1 a procedure was given to validate your correspondents' public keys: a correspondent's key is validated by personally checking his key's fingerprint and then signing his public key with your private key. By personally checking the fingerprint you can be sure that the key really does belong to him, and since you have signed they key, you can be sure to detect any tampering with it in the future. Unfortunately, this procedure is awkward when either you must validate a large number of keys or communicate with people whom you do not know personally.
GnuPG addresses this problem with a mechanism popularly known as the web of trust. In the web of trust model, responsibility for validating public keys is delegated to people you trust. For example, suppose
- Alice has signed Blake's key, and
- Blake has signed Chloe's key and Dharma's key.
If Alice trusts Blake to properly validate keys that he signs, then Alice can infer that Chloe's and Dharma's keys are valid without having to personally check them. She simply uses her validated copy of Blake's public key to check that Blake's signatures on Chloe's and Dharma's are good. In general, assuming that Alice fully trusts everybody to properly validate keys they sign, then any key signed by a valid key is also considered valid. The root is Alice's key, which is axiomatically assumed to be valid.
Trust in a key's owner
In practice trust is subjective. For example, Blake's key is valid to Alice since she signed it, but she may not trust Blake to properly validate keys that he signs. In that case, she would not take Chloe's and Dharma's key as valid based on Blake's signatures alone. The web of trust model accounts for this by associating with each public key on your keyring an indication of how much you trust the key's owner. There are four trust levels.
unknown
Nothing is known about the owner's judgment in key signing. Keys on your public keyring that you do not own initially have this trust level.
none
The owner is known to improperly sign other keys.
marginal
The owner understands the implications of key signing and properly validates keys before signing them.
full
The owner has an excellent understanding of key signing, and his signature on a key would be as good as your own.
A key's trust level is something that you alone assign to the key, and it is considered private information. It is not packaged with the key when it is exported; it is even stored separately from your keyrings in a separate database.
The GnuPG key editor may be used to adjust your trust in a key's owner. The command is trust. In this example Alice edits her trust in Blake and then updates the trust database to recompute which keys are valid based on her new trust in Blake.
alice% gpg --edit-key blake pub 1024D/8B927C8A created: 1999-07-02 expires: never trust: q/f sub 1024g/C19EA233 created: 1999-07-02 expires: never (1) Blake (Executioner) <blake@cyb.org> Command> trust pub 1024D/8B927C8A created: 1999-07-02 expires: never trust: q/f sub 1024g/C19EA233 created: 1999-07-02 expires: never (1) Blake (Executioner) <blake@cyb.org>
Please decide how far you trust this user to correctly verify other users' keys (by looking at passports, checking fingerprints from different sources...)? 1 = Don't know 2 = I do NOT trust 3 = I trust marginally 4 = I trust fully s = please show me more information m = back to the main menu Your decision? 3 pub 1024D/8B927C8A created: 1999-07-02 expires: never trust: m/f sub 1024g/C19EA233 created: 1999-07-02 expires: never (1) Blake (Executioner) <blake@cyb.org> Command> quit [...]
Trust in the key's owner and the key's validity are indicated to the right when the key is displayed. Trust in the owner is displayed first and the key's validity is second[4]. The four trust/validity levels are abbreviated: unknown (q), none (n), marginal (m), and full (f). In this case, Blake's key is fully valid since Alice signed it herself. She initially has an unknown trust in Blake to properly sign other keys but decides to trust him marginally.
Using trust to validate keys
The web of trust allows a more elaborate algorithm to be used to validate a key. Formerly, a key was considered valid only if you signed it personally. A more flexible algorithm can now be used: a key K is considered valid if it meets two conditions:
1. it is signed by enough valid keys, meaning
* you have signed it personally,
* it has been signed by one fully trusted key, or
* it has been signed by three marginally trusted keys; and
2. the path of signed keys leading from K back to your own key is five steps or shorter.
The path length, number of marginally trusted keys required, and number of fully trusted keys required may be adjusted. The numbers given above are the default values used by GnuPG.
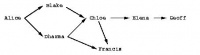
Figure 3-1 shows a web of trust rooted at Alice. The graph illustrates who has signed who's keys. The table shows which keys Alice considers valid based on her trust in the other members of the web. This example assumes that two marginally-trusted keys or one fully-trusted key is needed to validate another key. The maximum path length is three.
When computing valid keys in the example, Blake and Dharma's are always considered fully valid since they were signed directly by Alice. The validity of the other keys depends on trust. In the first case, Dharma is trusted fully, which implies that Chloe's and Francis's keys will be considered valid. In the second example, Blake and Dharma are trusted marginally. Since two marginally trusted keys are needed to fully validate a key, Chloe's key will be considered fully valid, but Francis's key will be considered only marginally valid. In the case where Chloe and Dharma are marginally trusted, Chloe's key will be marginally valid since Dharma's key is fully valid. Francis's key, however, will also be considered marginally valid since only a fully valid key can be used to validate other keys, and Dharma's key is the only fully valid key that has been used to sign Francis's key. When marginal trust in Blake is added, Chloe's key becomes fully valid and can then be used to fully validate Francis's key and marginally validate Elena's key. Lastly, when Blake, Chloe, and Elena are fully trusted, this is still insufficient to validate Geoff's key since the maximum certification path is three, but the path length from Geoff back to Alice is four.
The web of trust model is a flexible approach to the problem of safe public key exchange. It permits you to tune GnuPG to reflect how you use it. At one extreme you may insist on multiple, short paths from your key to another key K in order to trust it. On the other hand, you may be satisfied with longer paths and perhaps as little as one path from your key to the other key K. Requiring multiple, short paths is a strong guarantee that K belongs to whom your think it does. The price, of course, is that it is more difficult to validate keys since you must personally sign more keys than if you accepted fewer and longer paths.
A graph indicating who has signed who's key
trust validity marginal full marginal full Dharma Blake, Chloe, Dharma, Francis Blake, Dharma Francis Blake, Chloe, Dharma Chloe, Dharma Chloe, Francis Blake, Dharma Blake, Chloe, Dharma Elena Blake, Chloe, Dharma, Francis Blake, Chloe, Elena Blake, Chloe, Elena, Francis
Distributing keys
Ideally, you distribute your key by personally giving it to your correspondents. In practice, however, keys are often distributed by email or some other electronic communication medium. Distribution by email is good practice when you have only a few correspondents, and even if you have many correspondents, you can use an alternative means such as posting your public key on your World Wide Web homepage. This is unacceptable, however, if people who need your public key do not know where to find it on the Web.
To solve this problem public key servers are used to collect and distribute public keys. A public key received by the server is either added to the server's database or merged with the existing key if already present. When a key request comes to the server, the server consults its database and returns the requested public key if found.
A keyserver is also valuable when many people are frequently signing other people's keys. Without a keyserver, when Blake sign's Alice's key then Blake would send Alice a copy of her public key signed by him so that Alice could add the updated key to her ring as well as distribute it to all of her correspondents. Going through this effort fulfills Alice's and Blake's responsibility to the community at large in building tight webs of trust and thus improving the security of PGP. It is nevertheless a nuisance if key signing is frequent.
Using a keyserver makes the process somewhat easier. When Blake signs Alice's key he sends the signed key to the key server. The key server adds Blake's signature to its copy of Alice's key. Individuals interested in updating their copy of Alice's key then consult the keyserver on their own initiative to retrieve the updated key. Alice need never be involved with distribution and can retrieve signatures on her key simply by querying a keyserver.
One or more keys may be sent to a keyserver using the command-line option --send-keys. The option takes one or more key specifiers and sends the specified keys to the key server. The key server to which to send the keys is specified with the command-line option --keyserver. Similarly, the option --recv-keys is used to retrieve keys from a keyserver, but the option --recv-keys requires a key ID be used to specify the key. In the following example Alice updates her public key with new signatures from the keyserver certserver.pgp.com and then sends her copy of Blake's public key to the same keyserver to contribute any new signatures she may have added.
alice% gpg --keyserver certserver.pgp.com --recv-key 0xBB7576AC gpg: requesting key BB7576AC from certserver.pgp.com ... gpg: key BB7576AC: 1 new signature gpg: Total number processed: 1 gpg: new signatures: 1 alice% gpg --keyserver certserver.pgp.com --send-key blake@cyb.org gpg: success sending to 'certserver.pgp.com' (status=200)
There are several popular keyservers in use around the world. The major keyservers synchronize themselves, so it is fine to pick a keyserver close to you on the Internet and then use it regularly for sending and receiving keys.
Chapter 4. Daily use of GnuPG
GnuPG is a complex tool with technical, social, and legal issues surrounding it. Technically, it has been designed to be used in situations having drastically different security needs. This complicates key management. Socially, using GnuPG is not strictly a personal decision. To use GnuPG effectively both parties communicating must use it. Finally, as of 1999, laws regarding digital encryption, and in particular whether or not using GnuPG is legal, vary from country to country and is currently being debated by many national governments.
This chapter addresses these issues. It gives practical advice on how to use GnuPG to meet your security needs. It also suggests ways to promote the use of GnuPG for secure communication between yourself and your colleagues when your colleagues are not currently using GnuPG. Finally, the legal status of GnuPG is outlined given the current status of encryption laws in the world. Defining your security needs
GnuPG is a tool you use to protect your privacy. Your privacy is protected if you can correspond with others without eavesdroppers reading those messages.
How you should use GnuPG depends on the determination and resourcefulness of those who might want to read your encrypted messages. An eavesdropper may be an unscrupulous system administrator casually scanning your mail, it might be an industrial spy trying to collect your company's secrets, or it might be a law enforcement agency trying to prosecute you. Using GnuPG to protect against casual eavesdropping is going to be different than using GnuPG to protect against a determined adversary. Your goal, ultimately, is to make it more expensive to recover the unencrypted data than that data is worth.
Customizing your use of GnuPG revolves around four issues:
- choosing the key size of your public/private keypair,
- protecting your private key,
- selecting expiration dates and using subkeys, and
- managing your web of trust.
A well-chosen key size protects you against brute-force attacks on encrypted messages. Protecting your private key prevents an attacker from simply using your private key to decrypt encrypted messages and sign messages in your name. Correctly managing your web of trust prevents attackers from masquerading as people with whom you communicate. Ultimately, addressing these issues with respect to your own security needs is how you balance the extra work required to use GnuPG with the privacy it gives you.
Choosing a key size
Selecting a key size depends on the key. In OpenPGP, a public/private keypair usually has multiple keys. At the least it has a master signing key, and it probably has one or more additional subkeys for encryption. Using default key generation parameters with GnuPG, the master key will be a DSA key, and the subkeys will be ElGamal keys.
DSA allows a key size up to 1024 bits. This is not especially good given today's factoring technology, but that is what the standard specifies. Without question, you should use 1024 bit DSA keys.
ElGamal keys, on the other hand, may be of any size. Since GnuPG is a hybrid public-key system, the public key is used to encrypt a 128-bit session key, and the private key is used to decrypt it. Key size nevertheless affects encryption and decryption speed since the cost of these algorithms is exponential in the size of the key. Larger keys also take more time to generate and take more space to store. Ultimately, there are diminishing returns on the extra security a large key provides you. After all, if the key is large enough to resist a brute-force attack, an eavesdropper will merely switch to some other method for obtaining your plaintext data. Examples of other methods include robbing your home or office and mugging you. 1024 bits is thus the recommended key size. If you genuinely need a larger key size then you probably already know this and should be consulting an expert in data security.
Protecting your private key
Protecting your private key is the most important job you have to use GnuPG correctly. If someone obtains your private key, then all data encrypted to the private key can be decrypted and signatures can be made in your name. If you lose your private key, then you will no longer be able to decrypt documents encrypted to you in the future or in the past, and you will not be able to make signatures. Losing sole possession of your private key is catastrophic.
Regardless of how you use GnuPG you should store the public key's revocation certificate and a backup of your private key on write-protected media in a safe place. For example, you could burn them on a CD-ROM and store them in your safe deposit box at the bank in a sealed envelope. Alternatively, you could store them on a floppy and hide it in your house. Whatever you do, they should be put on media that is safe to store for as long as you expect to keep the key, and you should store them more carefully than the copy of your private key you use daily.
To help safeguard your key, GnuPG does not store your raw private key on disk. Instead it encrypts it using a symmetric encryption algorithm. That is why you need a passphrase to access the key. Thus there are two barriers an attacker must cross to access your private key: (1) he must actually acquire the key, and (2) he must get past the encryption.
Safely storing your private key is important, but there is a cost. Ideally, you would keep the private key on a removable, write-protected disk such as a floppy disk, and you would use it on a single-user machine not connected to a network. This may be inconvenient or impossible for you to do. For example, you may not own your own machine and must use a computer at work or school, or it may mean you have to physically disconnect your computer from your cable modem every time you want to use GnuPG.
This does not mean you cannot or should not use GnuPG. It means only that you have decided that the data you are protecting is important enough to encrypt but not so important as to take extra steps to make the first barrier stronger. It is your choice.
A good passphrase is absolutely critical when using GnuPG. Any attacker who gains access to your private key must bypass the encryption on the private key. Instead of brute-force guessing the key, an attacker will almost certainly instead try to guess the passphrase.
The motivation for trying passphrases is that most people choose a passphrase that is easier to guess than a random 128-bit key. If the passphrase is a word, it is much cheaper to try all the words in the dictionaries of the world's languages. Even if the word is permuted, e.g., k3wldood, it is still easier to try dictionary words with a catalog of permutations. The same problem applies to quotations. In general, passphrases based on natural-language utterances are poor passphrases since there is little randomness and lots of redundancy in natural language. You should avoid natural language passphrases if you can.
A good passphrase is one that you can remember but is hard for someone to guess. It should include characters from the whole range of printable characters on your keyboard. This includes uppercase alphabetics characters, numbers, and special characters such as } and |. Be creative and spend a little time considering your passphrase; a good choice is important to ensure your privacy.
Selecting expiration dates and using subkeys
By default, a DSA master signing key and an ElGamal encryption subkey are generated when you create a new keypair. This is convenient, because the roles of the two keys are different, and you may therefore want the keys to have different lifetimes. The master signing key is used to make digital signatures, and it also collects the signatures of others who have confirmed your identity. The encryption key is used only for decrypting encrypted documents sent to you. Typically, a digital signature has a long lifetime, e.g., forever, and you also do not want to lose the signatures on your key that you worked hard to collect. On the other hand, the encryption subkey may be changed periodically for extra security, since if an encryption key is broken, the attacker can read all documents encrypted to that key both in the future and from the past.
It is almost always the case that you will not want the master key to expire. There are two reasons why you may choose an expiration date. First, you may intend for the key to have a limited lifetime. For example, it is being used for an event such as a political campaign and will no longer be useful after the campaign is over. Another reason is that if you lose control of the key and do not have a revocation certificate with which to revoke the key, having an expiration date on the master key ensures that the key will eventually fall into disuse.
Changing encryption subkeys is straightforward but can be inconvenient. If you generate a new keypair with an expiration date on the subkey, that subkey will eventually expire. Shortly before the expiration you will add a new subkey and publish your updated public key. Once the subkey expires, those who wish to correspond with you must find your updated key since they will no longer be able to encrypt to the expired key. This may be inconvenient depending on how you distribute the key. Fortunately, however, no extra signatures are necessary since the new subkey will have been signed with your master signing key, which presumably has already been validated by your correspondents.
The inconvenience may or may not be worth the extra security. Just as you can, an attacker can still read all documents encrypted to an expired subkey. Changing subkeys only protects future documents. In order to read documents encrypted to the new subkey, the attacker would need to mount a new attack using whatever techniques he used against you the first time.
Finally, it only makes sense to have one valid encryption subkey on a keyring. There is no additional security gained by having two or more active subkeys. There may of course be any number of expired keys on a keyring so that documents encrypted in the past may still be decrypted, but only one subkey needs to be active at any given time.
Managing your web of trust
As with protecting your private key, managing your web of trust is another aspect of using GnuPG that requires balancing security against ease of use. If you are using GnuPG to protect against casual eavesdropping and forgeries then you can afford to be relatively trusting of other people's signatures. On the other hand, if you are concerned that there may be a determined attacker interested in invading your privacy, then you should be much less trusting of other signatures and spend more time personally verifying signatures.
Regardless of your own security needs, though, you should always be careful when signing other keys. It is selfish to sign a key with just enough confidence in the key's validity to satisfy your own security needs. Others, with more stringent security needs, may want to depend on your signature. If they cannot depend on you then that weakens the web of trust and makes it more difficult for all GnuPG users to communicate. Use the same care in signing keys that you would like others to use when you depend on their signatures.
In practice, managing your web of trust reduces to assigning trust to others and tuning the options --marginals-needed and --completes-needed. Any key you personally sign will be considered valid, but except for small groups, it will not be practical to personally sign the key of every person with whom you communicate. You will therefore have to assign trust to others.
It is probably wise to be accurate when assigning trust and then use the options to tune how careful GnuPG is with key validation. As a concrete example, you may fully trust a few close friends that you know are careful with key signing and then marginally trust all others on your keyring. From there, you may set --completes-needed to 1 and --marginals-needed to 2. If you are more concerned with security you might choose values of 1 and 3 or 2 and 3 respectively. If you are less concerned with privacy attacks and just want some reasonable confidence about validity, set the values to 1 and 1. In general, higher numbers for these options imply that more people would be needed to conspire against you in order to have a key validated that does not actually belong to the person whom you think it does.
Building your web of trust
Wanting to use GnuPG yourself is not enough. In order to use to communicate securely with others you must have a web of trust. At first glance, however, building a web of trust is a daunting task. The people with whom you communicate need to use GnuPG[5], and there needs to be enough key signing so that keys can be considered valid. These are not technical problems; they are social problems. Nevertheless, you must overcome these problems if you want to use GnuPG.
When getting started using GnuPG it is important to realize that you need not securely communicate with every one of your correspondents. Start with a small circle of people, perhaps just yourself and one or two others who also want to exercise their right to privacy. Generate your keys and sign each other's public keys. This is your initial web of trust. By doing this you will appreciate the value of a small, robust web of trust and will be more cautious as you grow your web in the future.
In addition to those in your initial web of trust, you may want to communicate securely with others who are also using GnuPG. Doing so, however, can be awkward for two reasons: (1) you do not always know when someone uses or is willing to use GnuPG, and (2) if you do know of someone who uses it, you may still have trouble validating their key. The first reason occurs because people do not always advertise that they use GnuPG. The way to change this behavior is to set the example and advertise that you use GnuPG. There are at least three ways to do this: you can sign messages you mail to others or post to message boards, you can put your public key on your web page, or, if you put your key on a keyserver, you can put your key ID in your email signature. If you advertise your key then you make it that much more acceptable for others to advertise their keys. Furthermore, you make it easier for others to start communicating with you securely since you have taken the initiative and made it clear that you use GnuPG.
Key validation is more difficult. If you do not personally know the person whose key you want to sign, then it is not possible to sign the key yourself. You must rely on the signatures of others and hope to find a chain of signatures leading from the key in question back to your own. To have any chance of finding a chain, you must take the initiative and get your key signed by others outside of your initial web of trust. An effective way to accomplish this is to participate in key signing parties. If you are going to a conference look ahead of time for a key signing party, and if you do not see one being held, offer to hold one. You can also be more passive and carry your fingerprint with you for impromptu key exchanges. In such a situation the person to whom you gave the fingerprint would verify it and sign your public key once he returned home.
Keep in mind, though, that this is optional. You have no obligation to either publicly advertise your key or sign other people's keys. The power of GnuPG is that it is flexible enough to adapt to your security needs whatever they may be. The social reality, however, is that you will need to take the initiative if you want to grow your web of trust and use GnuPG for as much of your communication as possible. Using GnuPG legally
The legal status of encryption software varies from country to country, and law regarding encryption software is rapidly evolving. Bert-Japp Koops has an excellent Crypto Law Survey to which you should refer for the legal status of encryption software in your country.
Chapter 5. Topics
This chapter covers miscellaneous topics that do not fit elsewhere in the user manual. As topics are added, they may be collected and factored into chapters that stand on their own. If you would like to see a particular topic covered, please suggest it. Even better, volunteer to write a first draft covering your suggested topic! Writing user interfaces
Alma Whitten and Doug Tygar have done a study on NAI's PGP 5.0 user interface and came to the conclusion that novice users find PGP confusing and frustrating. In their human factors study, only four out of twelve test subjects managed to correctly send encrypted email to their team members, and three out of twelve emailed the secret without encryption. Furthermore, half of the test subjects had a technical background.
These results are not surprising. PGP 5.0 has a nice user interface that is excellent if you already understand how public-key encryption works and are familiar with the web-of-trust key management model specified by OpenPGP. Unfortunately, novice users understand neither public-key encryption nor key management, and the user interface does little to help.
You should certainly read Whitten and Tygar's report if you are writing a user interface. It gives specific comments from each of the test subjects, and those details are enlightening. For example, it would appear that many of subjects believed that a message being sent to other people should be encrypted to the test subject's own public key. Consider it for a minute, and you will see that it is an easy mistake to make. In general, novice users have difficulty understanding the different roles of the public key and private key when using GnuPG. As a user interface designer, you should try to make it clear at all times when one of the two keys is being used. You could also use wizards or other common GUI techniques for guiding the user through common tasks, such as key generation, where extra steps, such as generating a key revocation certification and making a backup, are all but essential for using GnuPG correctly. Other comments from the paper include the following.
- Security is usually a secondary goal; people want to send email, browse, and so on. Do not assume users will be motivated to read manuals or go looking for security controls.
- The security of a networked computer is only as strong as its weakest component. Users need to be guided to attend to all aspects of their security, not left to proceed through random exploration as they might with a word processor or a spreadsheet.
- Consistently use the same terms for the same actions. Do not alternate between synonyms like ``encrypt and ``encipher.
- For inexperienced users, simplify the display. Too much information hides the important information. An initial display configuration could concentrate on giving the user the correct model of the relationship between public and private keys and a clear understanding of the functions for acquiring and distributing keys.
Designing an effective user interface for key management is even more difficult. The OpenPGP web-of-trust model is unfortunately quite obtuse. For example, the specification imposes three arbitrary trust levels onto the user: none, marginal, and complete. All degrees of trust felt by the user must be fit into one of those three cubbyholes. The key validation algorithm is also difficult for non-computer scientists to understand, particularly the notions of ``marginals needed and ``completes needed. Since the web-of-trust model is well-specified and cannot be changed, you will have to do your best and design a user interface that helps to clarify it for the user. A definite improvement, for example, would be to generate a diagram of how a key was validated when requested by the user. Relevant comments from the paper include the following.
- Users are likely to be uncertain on how and when to grant accesses.
- Place a high priority on making sure users understand their security well enough to prevent them from making potentially high-cost mistakes. Such mistakes include accidentally deleting the private key, accidentally publicizing a key, accidentally revoking a key, forgetting the pass phrase, and failing to back up the key rings.
Notes
[1] Option 3 is to generate an ElGamal keypair that is not usable for making signatures. [2] Many command-line options that are frequently used can also be set in a configuration file. [3] The cipher must have the property that the actual public key or private key could be used by the encryption algorithm as the public key. RSA is an example of such an algorithm while ElGamal is not an example. [4] GnuPG overloads the word ``trust by using it to mean trust in an owner and trust in a key. This can be confusing. Sometimes trust in an owner is referred to as owner-trust to distinguish it from trust in a key. Throughout this manual, however, ``trust is used to mean trust in a key's owner, and ``validity is used to mean trust that a key belongs to the human associated with the key ID. [5] In this section, GnuPG refers to the GnuPG implementation of OpenPGP as well as other implementations such as NAI's PGP product.