Difference between revisions of "Mikrotik: OpenVPN - Server ke PC"
Onnowpurbo (talk | contribs) |
Onnowpurbo (talk | contribs) |
||
| (49 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
Sumber: https://www.medo64.com/2016/12/simple-openvpn-server-on-mikrotik/ | Sumber: https://www.medo64.com/2016/12/simple-openvpn-server-on-mikrotik/ | ||
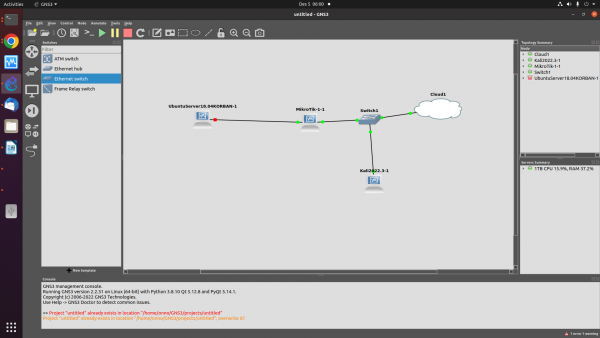
| + | Asumsi kita membuat sambungan OpenVPN dengan Server di balik Mikrotik sebagai berikut, | ||
| − | ==Certificate Generate== | + | [[File:Openvpn-mikrotik.png|center|600px|thumb]] |
| + | |||
| + | |||
| + | ==Setup Router Mikrotik Biasa== | ||
| + | |||
| + | /ip dhcp-client print | ||
| + | /ip dhcp-client add interface=ether1 disable=no | ||
| + | /interface bridge | ||
| + | add name=bridge1 | ||
| + | /interface bridge port | ||
| + | add bridge=bridge1 interface=ether2 | ||
| + | add bridge=bridge1 interface=ether3 | ||
| + | add bridge=bridge1 interface=ether4 | ||
| + | add bridge=bridge1 interface=ether5 | ||
| + | add bridge=bridge1 interface=ether6 | ||
| + | add bridge=bridge1 interface=ether7 | ||
| + | add bridge=bridge1 interface=ether8 | ||
| + | /ip address add interface=bridge1 address=192.168.100.1/24 | ||
| + | /ip route add gateway=bridge1 | ||
| + | /ip dns set servers=1.1.1.1 | ||
| + | /ip dns set allow-remote-request=yes | ||
| + | /ip firewall nat add chain=srcnat out-interface=ether1 action=masquerade | ||
| + | /ip firewall nat print | ||
| + | |||
| + | /ip dhcp-server setup | ||
| + | |||
| + | ==Certificate== | ||
| + | |||
| + | ===Certificate Generate=== | ||
/certificate | /certificate | ||
| Line 11: | Line 40: | ||
| − | ==Certificate Sign== | + | ===Certificate Sign=== |
| − | |||
| − | |||
| + | '''SATU PER SATU''', jangan COPAS Sekaligus. Proses signing akan membutuhkan waktu, harap sabar. | ||
/certificate | /certificate | ||
| Line 22: | Line 50: | ||
sign client1-template name=client1-certificate ca=ca-certificate | sign client1-template name=client1-certificate ca=ca-certificate | ||
| − | + | ===Certificate Trust=== | |
| − | ==Certificate Trust== | ||
/certificate | /certificate | ||
| Line 29: | Line 56: | ||
set server-certificate trusted=yes | set server-certificate trusted=yes | ||
| − | ==Certificate Export== | + | ===Certificate Export=== |
/certificate | /certificate | ||
export-certificate ca-certificate export-passphrase="" | export-certificate ca-certificate export-passphrase="" | ||
| − | export-certificate client-certificate export-passphrase= | + | export-certificate client-certificate export-passphrase=123456789 |
| − | export-certificate client1-certificate export-passphrase= | + | export-certificate client1-certificate export-passphrase=123456789 |
Cek bahwa sudah di generate menggunakan | Cek bahwa sudah di generate menggunakan | ||
/file print | /file print | ||
| + | |||
| + | ==OpenVPN Server di Mikrotik== | ||
| + | |||
| + | |||
| + | ===OpenVPN Pool Address=== | ||
| + | |||
| + | /ip | ||
| + | pool add name="vpn-pool" ranges=192.168.8.10-192.168.8.99 | ||
| + | |||
| + | ===OpenVPN user=== | ||
| + | |||
| + | /ppp | ||
| + | profile add name="vpn-profile" use-encryption=yes local-address=192.168.8.250 dns-server=192.168.8.250 remote-address=vpn-pool | ||
| + | secret add name=user profile=vpn-profile password=123456 | ||
| + | secret add name=user1 profile=vpn-profile password=123456 | ||
| + | secret add name=user2 profile=vpn-profile password=123456 | ||
| + | secret add name=onno profile=vpn-profile password=123456 | ||
| + | |||
| + | ===OpenVPN Enable=== | ||
| + | |||
| + | /interface ovpn-server server | ||
| + | set default-profile=vpn-profile certificate=server-certificate require-client-certificate=yes auth=sha1 cipher=aes128,aes192,aes256 enabled=yes | ||
| + | |||
| + | |||
| + | ==Set Firewall Mikrotik== | ||
| + | |||
| + | Jika dibutuhkan kita bisa buka access port 1194 | ||
| + | |||
| + | /ip firewall filter | ||
| + | add chain=input protocol=tcp dst-port=1194 action=accept place-before=0 comment="Allow OpenVPN" | ||
| + | |||
| + | atau | ||
| + | |||
| + | /ip firewall filter | ||
| + | add chain=input protocol=tcp dst-port=1194 action=accept comment="Allow OpenVPN" | ||
| + | |||
| + | ==PC Kali Linux== | ||
| + | |||
| + | ===Download crt & key=== | ||
| + | |||
| + | cd /etc/openvpn/client | ||
| + | |||
| + | ftp 192.168.0.219 # IP OpenVPN Mikrotik | ||
| + | username admin | ||
| + | password | ||
| + | mget * | ||
| + | quit | ||
| + | |||
| + | ===Edit client.ovpn=== | ||
| + | |||
| + | cd /etc/openvpn/client | ||
| + | vi client.ovpn | ||
| + | |||
| + | client | ||
| + | dev tun | ||
| + | proto tcp | ||
| + | # remote (IP Mikrotik OpenVPN) 1194 | ||
| + | remote 192.168.0.219 1194 | ||
| + | resolv-retry infinite | ||
| + | nobind | ||
| + | persist-key | ||
| + | persist-tun | ||
| + | ca /etc/openvpn/client/cert_export_ca-certificate.crt | ||
| + | cert /etc/openvpn/client/cert_export_client-certificate.crt | ||
| + | key /etc/openvpn/client/cert_export_client-certificate.key | ||
| + | remote-cert-tls server | ||
| + | cipher AES-256-CBC | ||
| + | auth SHA1 | ||
| + | auth-user-pass | ||
| + | route 192.168.100.0 255.255.255.0 # Paksakan routing di belakang Mikrotik | ||
| + | |||
| + | ===PC Run OpenVPN=== | ||
| + | |||
| + | cd /etc/openvpn/client | ||
| + | sudo openvpn --config client.ovpn | ||
| + | |||
| + | Enter Auth Username: user | ||
| + | Enter Auth Password: 123456 | ||
| + | Enter Private Key Password: 123456789 | ||
| + | |||
| + | ===Interface tun tambahan=== | ||
| + | |||
| + | Di CLI Kali Linux, ketik | ||
| + | |||
| + | ifconfig | ||
| + | |||
| + | Jika OpenVPN Berhasil di aktifkan, akan muncul | ||
| + | |||
| + | tun0: flags=4305<UP,POINTOPOINT,RUNNING,NOARP,MULTICAST> mtu 1500 | ||
| + | inet 192.168.8.99 netmask 255.255.255.0 destination 192.168.8.99 | ||
| + | inet6 fe80::959a:7bd0:a3f3:3cc6 prefixlen 64 scopeid 0x20<link> | ||
| + | unspec 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00 txqueuelen 500 (UNSPEC) | ||
| + | RX packets 0 bytes 0 (0.0 B) | ||
| + | RX errors 0 dropped 0 overruns 0 frame 0 | ||
| + | TX packets 22 bytes 2384 (2.3 KiB) | ||
| + | TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 | ||
| + | |||
| + | |||
| + | ===Tambahkan Routing ke LAN di Belakang Mikrotik=== | ||
| + | |||
| + | route add -net 192.168.100.0/24 gw 192.168.8.250 dev tun0 | ||
| + | |||
| + | ==PC Client== | ||
| + | |||
| + | ===PC Download File=== | ||
Bisa di download ke PC / client menggunakan ftp, file yang dibutuhkan adalah | Bisa di download ke PC / client menggunakan ftp, file yang dibutuhkan adalah | ||
| Line 51: | Line 183: | ||
| − | + | dengan ftp | |
| + | |||
| + | cd /etc/openvpn/client | ||
| + | ftp 192.168.88.198 | ||
| + | username admin | ||
| + | password | ||
| + | |||
| + | mget * | ||
| + | quit | ||
| + | |||
| + | |||
| + | cd /etc/openvpn/client | ||
| + | mv cert_export_ca-certificate.crt ca.crt | ||
| + | mv cert_export_client1-certificate.crt client1.crt | ||
| + | mv cert_export_client1-certificate.key client1.key | ||
| + | mv cert_export_client-certificate.crt client.crt | ||
| + | mv cert_export_client-certificate.key client.key | ||
| + | |||
| + | |||
| + | ===PC Buat Konfigurasi ovpn=== | ||
| + | |||
| + | Buat client.ovpn | ||
| + | |||
| + | cd /etc/openvpn/client/ | ||
| + | sudo vi client.ovpn | ||
| + | |||
| + | client | ||
| + | dev tun | ||
| + | proto tcp | ||
| + | # remote (IP OpenVPN Mikrotik) 1194 | ||
| + | remote 192.168.0.219 1194 | ||
| + | resolv-retry infinite | ||
| + | nobind | ||
| + | persist-key | ||
| + | persist-tun | ||
| + | ca ca.crt | ||
| + | cert client.crt | ||
| + | key client.key | ||
| + | remote-cert-tls server | ||
| + | cipher AES-128-CBC | ||
| + | auth SHA1 | ||
| + | auth-user-pass | ||
| + | # redirect-gateway def1 | ||
| + | |||
| + | ===PC Run OpenVPN=== | ||
| + | |||
| + | cd /etc/openvpn/client | ||
| + | sudo openvpn --config client.ovpn | ||
| + | |||
| + | Enter Auth Username: user | ||
| + | Enter Auth Password: password | ||
| + | Enter Private Key Password: 12345678 | ||
| + | |||
| + | |||
| + | ===PC Cek=== | ||
| + | |||
| + | Pastikan ada interface tun | ||
| + | |||
| + | ifconfig | ||
| + | |||
| + | tun0: flags=4305<UP,POINTOPOINT,RUNNING,NOARP,MULTICAST> mtu 1500 | ||
| + | inet 192.168.8.99 netmask 255.255.255.0 destination 192.168.8.99 | ||
| + | inet6 fe80::76b3:bffd:1b3a:b9ea prefixlen 64 scopeid 0x20<link> | ||
| + | unspec 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00 txqueuelen 100 (UNSPEC) | ||
| + | RX packets 1275 bytes 1208481 (1.2 MB) | ||
| + | RX errors 0 dropped 0 overruns 0 frame 0 | ||
| + | TX packets 1328 bytes 148649 (148.6 KB) | ||
| + | TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 | ||
| − | + | Pastikan ada routing | |
| − | + | netstat -nr | |
| − | |||
| − | |||
| − | + | 192.168.8.0 0.0.0.0 255.255.255.0 U 0 0 0 tun0 | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| + | ==Ubah client.key== | ||
| − | + | Langkah yang sedikit mengganggu adalah meminta kata private key password (selain username/password). Mikrotik tidak mengizinkan export key tanpa itu tapi untungnya kita bisa menggunakan OpenSSL untuk mengubahnya: | |
| − | |||
| − | + | openssl rsa -in client.key -out client.key | |
| − | |||
| − | |||
| − | |||
| − | + | Enter pass phrase for cert_export_client1.key: | |
| + | writing RSA key | ||
| − | |||
| − | |||
| − | |||
| − | + | Teknik ini bisa di coba2, tampaknya kita tetap harus memasukan username/password/private key password. | |
| − | |||
| − | |||
==Referensi== | ==Referensi== | ||
* https://www.medo64.com/2016/12/simple-openvpn-server-on-mikrotik/ | * https://www.medo64.com/2016/12/simple-openvpn-server-on-mikrotik/ | ||
Latest revision as of 18:47, 5 December 2022
Sumber: https://www.medo64.com/2016/12/simple-openvpn-server-on-mikrotik/
Asumsi kita membuat sambungan OpenVPN dengan Server di balik Mikrotik sebagai berikut,
Setup Router Mikrotik Biasa
/ip dhcp-client print /ip dhcp-client add interface=ether1 disable=no /interface bridge add name=bridge1 /interface bridge port add bridge=bridge1 interface=ether2 add bridge=bridge1 interface=ether3 add bridge=bridge1 interface=ether4 add bridge=bridge1 interface=ether5 add bridge=bridge1 interface=ether6 add bridge=bridge1 interface=ether7 add bridge=bridge1 interface=ether8 /ip address add interface=bridge1 address=192.168.100.1/24 /ip route add gateway=bridge1 /ip dns set servers=1.1.1.1 /ip dns set allow-remote-request=yes /ip firewall nat add chain=srcnat out-interface=ether1 action=masquerade /ip firewall nat print
/ip dhcp-server setup
Certificate
Certificate Generate
/certificate add name=ca-template common-name=example.com days-valid=3650 key-size=2048 key-usage=crl-sign,key-cert-sign add name=server-template common-name=*.example.com days-valid=3650 key-size=2048 key-usage=digital-signature,key-encipherment,tls-server add name=client-template common-name=client.example.com days-valid=3650 key-size=2048 key-usage=tls-client add name=client1-template common-name=client1.example.com days-valid=3650 key-size=2048 key-usage=tls-client
Certificate Sign
SATU PER SATU, jangan COPAS Sekaligus. Proses signing akan membutuhkan waktu, harap sabar.
/certificate sign ca-template name=ca-certificate sign server-template name=server-certificate ca=ca-certificate sign client-template name=client-certificate ca=ca-certificate sign client1-template name=client1-certificate ca=ca-certificate
Certificate Trust
/certificate set ca-certificate trusted=yes set server-certificate trusted=yes
Certificate Export
/certificate export-certificate ca-certificate export-passphrase="" export-certificate client-certificate export-passphrase=123456789 export-certificate client1-certificate export-passphrase=123456789
Cek bahwa sudah di generate menggunakan
/file print
OpenVPN Server di Mikrotik
OpenVPN Pool Address
/ip pool add name="vpn-pool" ranges=192.168.8.10-192.168.8.99
OpenVPN user
/ppp profile add name="vpn-profile" use-encryption=yes local-address=192.168.8.250 dns-server=192.168.8.250 remote-address=vpn-pool secret add name=user profile=vpn-profile password=123456 secret add name=user1 profile=vpn-profile password=123456 secret add name=user2 profile=vpn-profile password=123456 secret add name=onno profile=vpn-profile password=123456
OpenVPN Enable
/interface ovpn-server server set default-profile=vpn-profile certificate=server-certificate require-client-certificate=yes auth=sha1 cipher=aes128,aes192,aes256 enabled=yes
Set Firewall Mikrotik
Jika dibutuhkan kita bisa buka access port 1194
/ip firewall filter add chain=input protocol=tcp dst-port=1194 action=accept place-before=0 comment="Allow OpenVPN"
atau
/ip firewall filter add chain=input protocol=tcp dst-port=1194 action=accept comment="Allow OpenVPN"
PC Kali Linux
Download crt & key
cd /etc/openvpn/client
ftp 192.168.0.219 # IP OpenVPN Mikrotik username admin password mget * quit
Edit client.ovpn
cd /etc/openvpn/client vi client.ovpn
client dev tun proto tcp # remote (IP Mikrotik OpenVPN) 1194 remote 192.168.0.219 1194 resolv-retry infinite nobind persist-key persist-tun ca /etc/openvpn/client/cert_export_ca-certificate.crt cert /etc/openvpn/client/cert_export_client-certificate.crt key /etc/openvpn/client/cert_export_client-certificate.key remote-cert-tls server cipher AES-256-CBC auth SHA1 auth-user-pass route 192.168.100.0 255.255.255.0 # Paksakan routing di belakang Mikrotik
PC Run OpenVPN
cd /etc/openvpn/client sudo openvpn --config client.ovpn
Enter Auth Username: user Enter Auth Password: 123456 Enter Private Key Password: 123456789
Interface tun tambahan
Di CLI Kali Linux, ketik
ifconfig
Jika OpenVPN Berhasil di aktifkan, akan muncul
tun0: flags=4305<UP,POINTOPOINT,RUNNING,NOARP,MULTICAST> mtu 1500
inet 192.168.8.99 netmask 255.255.255.0 destination 192.168.8.99
inet6 fe80::959a:7bd0:a3f3:3cc6 prefixlen 64 scopeid 0x20<link>
unspec 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00 txqueuelen 500 (UNSPEC)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 22 bytes 2384 (2.3 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
Tambahkan Routing ke LAN di Belakang Mikrotik
route add -net 192.168.100.0/24 gw 192.168.8.250 dev tun0
PC Client
PC Download File
Bisa di download ke PC / client menggunakan ftp, file yang dibutuhkan adalah
cert_export_ca-certificate.crt cert_export_client-certificate.crt cert_export_client-certificate.key
Nantinya bisa di rename menjadi
ca.crt, client.crt, & client.key
dengan ftp
cd /etc/openvpn/client ftp 192.168.88.198 username admin password
mget * quit
cd /etc/openvpn/client mv cert_export_ca-certificate.crt ca.crt mv cert_export_client1-certificate.crt client1.crt mv cert_export_client1-certificate.key client1.key mv cert_export_client-certificate.crt client.crt mv cert_export_client-certificate.key client.key
PC Buat Konfigurasi ovpn
Buat client.ovpn
cd /etc/openvpn/client/ sudo vi client.ovpn
client dev tun proto tcp # remote (IP OpenVPN Mikrotik) 1194 remote 192.168.0.219 1194 resolv-retry infinite nobind persist-key persist-tun ca ca.crt cert client.crt key client.key remote-cert-tls server cipher AES-128-CBC auth SHA1 auth-user-pass # redirect-gateway def1
PC Run OpenVPN
cd /etc/openvpn/client sudo openvpn --config client.ovpn
Enter Auth Username: user Enter Auth Password: password Enter Private Key Password: 12345678
PC Cek
Pastikan ada interface tun
ifconfig
tun0: flags=4305<UP,POINTOPOINT,RUNNING,NOARP,MULTICAST> mtu 1500
inet 192.168.8.99 netmask 255.255.255.0 destination 192.168.8.99
inet6 fe80::76b3:bffd:1b3a:b9ea prefixlen 64 scopeid 0x20<link>
unspec 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00 txqueuelen 100 (UNSPEC)
RX packets 1275 bytes 1208481 (1.2 MB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 1328 bytes 148649 (148.6 KB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
Pastikan ada routing
netstat -nr
192.168.8.0 0.0.0.0 255.255.255.0 U 0 0 0 tun0
Ubah client.key
Langkah yang sedikit mengganggu adalah meminta kata private key password (selain username/password). Mikrotik tidak mengizinkan export key tanpa itu tapi untungnya kita bisa menggunakan OpenSSL untuk mengubahnya:
openssl rsa -in client.key -out client.key
Enter pass phrase for cert_export_client1.key: writing RSA key
Teknik ini bisa di coba2, tampaknya kita tetap harus memasukan username/password/private key password.